
TL;DR
- SaaS sprawl builds quietly through OAuth approvals and overlapping tools, so lock down your crown jewels first (email/docs, code repos, CRM, and HR) and check the rest with a light touch.
- SaaS security best practices don’t require a grand program: a monthly pass on new OAuth connections and a quarterly review of users, permissions, and shared links keeps access honest.
- AI in SaaS security works when you point it at the right problems: scope-heavy apps, dormant integrations, and over-shared docs that quietly pile up risk.
- Platforms like Sola turn scattered permissions into plain-language answers, so reviews become a quick pass instead of a click-by-click hunt through admin consoles.
Picture this: someone installs a “free” meeting helper before coffee, signs in with Google, and breezes past a prompt asking for “read, send, and delete email,” “view and manage all files,” and “access all calendars.” That is not a productivity boost, that is an excessive permissions starter pack. A few weeks later, you might be able to trace the approval, but it still has the keys.
SaaS sprawl works exactly like that: quiet approvals, overlapping tools, and no alert when sharing or access drifts. You do not need a grand program to fight it; you need a practical way to get your arms around what matters and keep it that way.
This SaaS security checklist is for teams that know they need control but do not have the appetite for expensive enterprise tooling. It focuses on your crown jewels first, keeps everything else on a light touch, and uses AI in SaaS security to turn messy permissions into clear actions: who has access to what, what changed, and what to fix next.
SaaS security is a mess for small teams
SaaS sprawl is real: teams sign up for what they need and move on, leaving a trail of permissions, overlapping tools, and quiet defaults. None of those apps tap you on the shoulder when access drifts or data gets shared too widely.
AI helps, but only when it is pointed at the right problems. The surge of AI tools has also added to the surface area, with more sign-ins and more permissions to manage, some of them clearly vibe-coded. The same way vibe coding security vulnerabilities creep into code when guardrails are thin, SaaS stacks collect risk when apps connect freely with no one tracking who has access to what.
So keep it simple. Start by deciding what actually matters, lock down the core systems where your data lives, and adopt a light, predictable cadence for checks. Then use AI to translate messy permissions into clear next steps: who has access to what, what changed since last month, and what should be fixed first.
The crown jewels: what actually matters in SaaS security
Start by naming the “crown jewels” of your stack, meaning the few systems that hold your most sensitive data and would cause real damage if exposed: Think email and docs with shared drives, code repositories, CRM, and the HR stack (if in scope). Treat these as tier one because this is where customer records, credentials, and internal information live. It is also where leaks trigger real pain and compliance heat.
Pick them by data, not by logo. Classify what sits where, across simple buckets like customer, employee and HR, and business or financial, with candidates and marketing analytics alongside; that lens makes priorities obvious. Then, create a single view by connecting your core systems and asking direct questions in one place, turning scattered permissions into a clear, actionable picture.
The full no-nonsense SaaS security checklist
No email required. Just grab and print.
Step 1: Map the chaos, then pick your battles
Kick off your SaaS security checklist by mapping what’s already wired into your org, then decide what actually deserves attention.
Do this now (with reasons):
- Run a quick Google Workspace security review to pull every third-party OAuth app users have approved. Why? because most sprawl starts with “Sign in with Google,” which quietly hands out scopes nobody audits.
- Tag the core apps that really hold sensitive data: email/docs & shared drives, code repos, CRM, and HR. Why these?
- Email/Docs & Drives: this is your company brain; links and sharing defaults leak fast if you don’t watch them.
- Code repos: beyond IP, they can contain tokens and configs. One sloppy repo can snowball into broader exposure.
- CRM: customer data and exports live here; it’s a trust and compliance landmine if mishandled.
- HR: the richest PII set and your “who’s actually employed” source of truth for access decisions.
- Classify by data type, not just app logo: group them into customer, employee/HR, and business/financial, so your priorities follow data impact rather than whichever vendor is loudest this week.
Where AI helps (usefully, not theatrically): once those sources are connected, AI assistants can highlight the crown jewels and flag over-broad scopes, so you spend minutes deciding, not days tab-hopping.
Step 2: Enforce onboarding, offboarding, and access control
Make access lifecycle boring (but in a good way!): predictable onboarding, clean changes, and zero leftovers on exit.
Do this now (with reasons):
- Onboard on rails: Give new hires a defined path into core apps, such as email, docs & shared drives, code repos and other critical applications for their work, all with default roles and SSO/MFA enforced. Why: ad-hoc invites turn into permissions you’ll never find (or clean up) later.
- Offboard with zero leftovers. Former employees shouldn’t retain access to anything – disable accounts, revoke access, and remove them from the core apps above. Why: lingering access is the most boring way to have a breach.
- Reclaim licenses, not just logins: Close the loop by pulling unused seats. Why: it saves money and prevents “zombie” access from reappearing at renewal.
- Use HR as the source of truth: HR holds the authoritative list of who actually works here. If HR marks someone inactive, every SaaS app should mirror that status. Why: using this single source for provisioning keeps access consistent and makes audits straightforward.
- Run lightweight access reviews on your top apps. Reconfirm roles and risky capabilities (admin/owner, exports) in email/docs, code, CRM, and HR. Why: roles drift; reviews catch it before it becomes your next incident.
Where AI helps (usefully, not theatrically): once HR and core apps are connected, let it answer plain-English questions like: “List users with export permissions in the CRM and ‘share externally’ in shared drives”. That’s minutes of triage instead of hours of digging permissions.
Step 3: Trace what’s connected to what (advanced; do basics first)
First pull the list of third-party apps your people approved; then look at app-to-app chains – those sequences where one SaaS feeds another (e.g., CRM ↔ Google Workspace ↔ HR). These chains matter because mistakes or over-broad access in one system can quietly spill into the next, multiplying your blast radius.
Useful? Absolutely. A must for day one? No – treat the deeper mapping as advanced work after Steps 1–2.
Do this now (with reasons):
- Re-export the apps list. Why: this is your node list for connection mapping, nothing else works without it.
- Prioritize connections that touch your crown jewels (your email, docs & shared drives, code repositories, CRM, HR platforms). Why: not every connection is necessarily risky; start with the ones tied to sensitive data.
- Advanced (optional): Map critical app-to-app flows (e.g., where CRM talks to Google Workspace and HR). Why: these chains expand blast radius, but mapping them is architecturally and operationally tougher – so it’s best to schedule it after the basics.
Where AI helps (usefully, not theatrically): once your sources are connected, with AI you can group connections by system and spotlight the “SaaS → SaaS → SaaS” loops you should review first, so you focus on chains that actually touch sensitive data instead of drowning in a flat list.
Step 4: Set a recurring review cadence
These checks are part of the job—keep them small, predictable, and focused on the core systems from Steps 1–3 so SaaS sprawl doesn’t creep back in.
Do this in cadence (with reasons):
- Monthly: Review new OAuth connections to your core systems. Why: approvals accumulate quietly; a monthly sweep catches fresh, scope-heavy add-ons before they become background noise.
- Monthly: Scan for public or widely shared links in shared storage (Drive/ SharePoint/ Box/ Dropbox or equivalent). Why: open links are the lowest-effort data leak; this keeps sharing sane without boiling the ocean.
- Quarterly: Review active users and permissions across your top 5 apps. Why: roles drift and “temporary” access lingers; a quarterly pass resets reality.
- Quarterly: Run an AI query or script to flag risky patterns (if available). Why: use AI for SaaS security to spotlight anomalies and summarize changes across the core apps, then move on.
Where AI helps (usefully, not theatrically): With your data already connected, let AI summarize changes and likely risks on a schedule, so each review is a quick pass rather than a click-by-click hunt through admin pages.
Adding AI to your workflows to complete the checklist
AI won’t run your security program for you, but it should take the output of your SaaS security checklist and answer the only questions that matter to you. What changed, what’s risky, and what do I fix next? It translates scattered permissions and scopes into a plain-English roadmap, so instead of spelunking across admin pages you move straight to decisions.
When you run the quarterly AI sweep (as required from the checklist’s 4th step), aim it at patterns that actually move risk. Here are a few examples:
- Scope-heavy third-party apps tied to your core-system. Trim or remove where it’s clearly over-broad.
- Public or widely shared links trend in your document stores. Tighten anything sensitive that drifted to “anyone with the link.”
- Dormant but privileged integrations (stale authorizations with high-impact scopes). Either fence them down or remove them.
- Non-human identities (service accounts, API keys, automations) with broad, long-lived access. Rotate, narrow, or gate them.
- If possible – Noisy app-to-app chains that touch sensitive systems. Schedule those for a focused review next cycle; they’re valuable but advanced.
Connect your core sources to Sola, ask in plain language, get an action list you can close. Files shared too widely, integrations with access to private repos, non-human identities with elevated permissions and more. Sola applies AI for SaaS security to keep the cadence simple and the work focused.
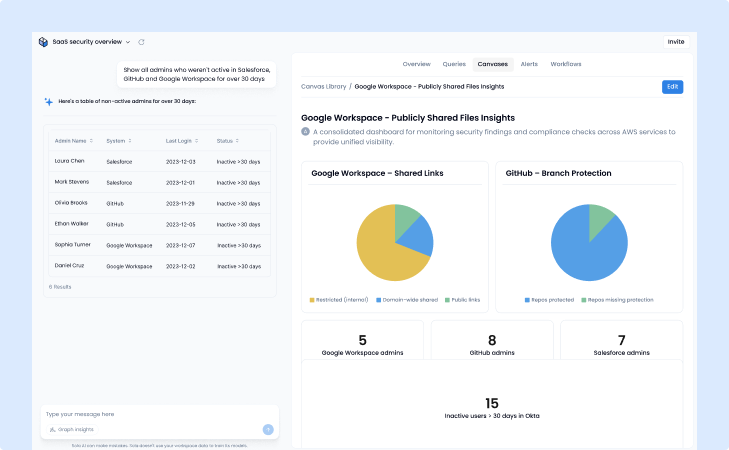
Summary: keeping SaaS sprawl in check, without overbuilding
You don’t need perfection, you need leverage. Chasing 100% coverage sounds noble, but the real win is a clear picture and a plan you can actually run. Start by deciding what matters, not what is loud.
Lock down the places that actually hold risk: email and docs with shared drives, code repos, CRM, and HR. Monitor the rest lightly and stick to a simple cadence: monthly for new apps/connections, quarterly for roles and permissions and over shared docs. Resist the urge to overbuild or overspend. That is how you keep the SaaS security checklist sustainable and how you chip away at SaaS sprawl.
AI is the accelerator, not the driver, so use it to turn the mess into actionable next steps. Let it flag scope heavy third party apps, dormant but privileged integrations, repo access that outgrew its purpose, non-human identities with long lived permissions, and links shared too widely, then act and move on. Done regularly, this turns endless audit into a fast loop of insight, fix, check in, which is exactly the point.
Create your SaaS security framework with Sola.
SaaS security FAQs
What is SaaS sprawl?
How to overcome SaaS sprawl?
Which solutions reduce SaaS sprawl by managing app access?
Which security measure is crucial for protecting user data in SaaS applications?
How does AI in SaaS security help small teams?
Strategic Advisor, Sola Security
Esther is a former CISO and seasoned security operator who bridges the real-world challenges security teams face with Sola’s solutions to maximize value, translating pain into product and strategy into execution. A strategic advisor at Sola and co-host of the 3rd Party podcast, she takes ideas from mic to roadmap with sharp, candid takes.
