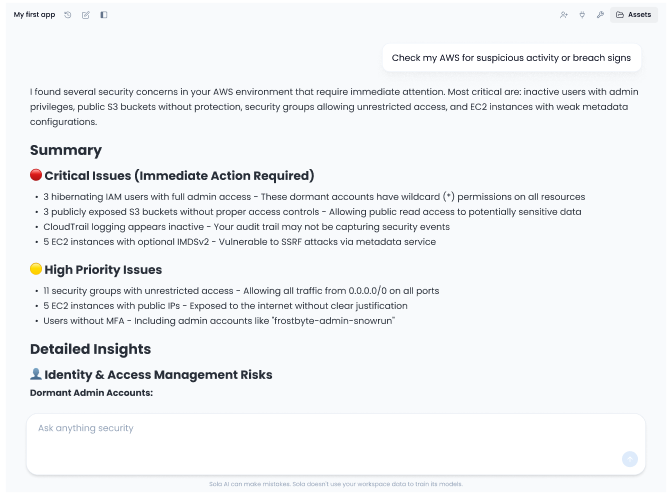
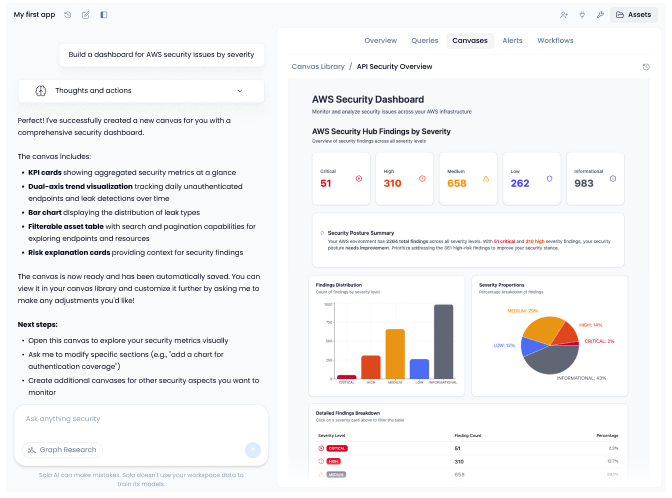
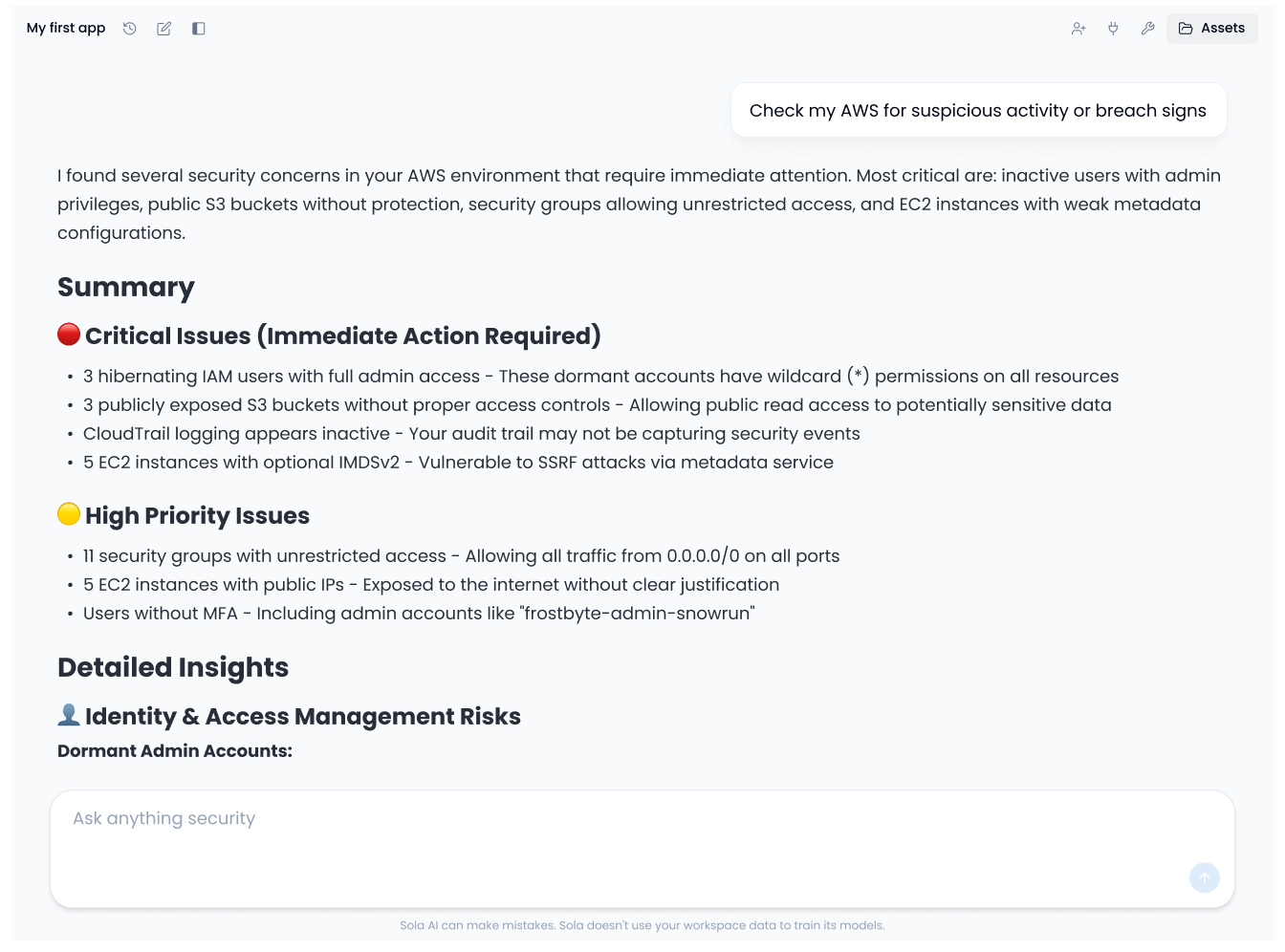
Connect your cloud, identity, SaaS, and code tools in minutes. Data is fed into your unified security graph, so one question can pull context across every tool instead of living in silos.
Everything stays read-only and Sola never touches more than it needs. Check out our Trust Center.