
Security teams are turning more and more to AI to speed up investigations and automate repetitive tasks to respond faster and more efficiently to threats. While looking into two of the main enablers, at first glance, they seem unrelated: one is the one-shot prompt security practitioners ask an LLM to “figure it out.” and the other is the traditional function-based automation tools. Both tools look great at first sight, but then wobble when real-world complexities come into play.
The next wave of addressing these cases and moving past the challenges of both tools lies in AI-native and multi-step processes. Let the model interpret and correlate, then move through small, structured steps that return more deterministic results you can inspect and reuse. You get the flexibility of AI with the reliability of defined execution. This is the approach Sola takes with agentic workflows.
In this article, we start with where single prompts and rigid automation fall short, and walk through how Sola’s agentic workflows operate step by step. We’ll also highlight what this unlocks for security teams – from simplifying multi-step investigations, through cleaner outputs, to continuous trustworthy flows across domains and tools.
Challenges with pure AI, one-shot prompts
Many security solutions, copilots and AI assistants rely on users issuing a single, powerful prompt to an LLM based tool, to analyze an incident or generate a response. While convenient in many cases, it often fluctuates in security operations due to:
- Black-box reasoning: A single prompt returns an answer without exposing the steps in between. You cannot see which signals mattered, what was ignored, or how confidence was determined
- Debugging nightmares: When the output is wrong, you cannot view it granularly and there is no place to isolate where exactly it failed.
- Context loss: As cases grow in size and complexity, the model loses earlier data. That leads to contradictions and incomplete responses.
- Non-deterministic outputs: The same input can lead to different results across runs, because of sampling and small timing differences.
- Drift across time: Model updates, provider changes, and small data shape shifts may break behavior without notice.
- Error propagation: If the first step misparses a user or IP, every downstream decision inherits the mistake. Without intermediate validation, one early miss corrupts the whole outcome.
Limitations of traditional automation tools
Another common path for security teams is using functional automations that script actions through fixed blocks and functions. They work when inputs match the script, but in reality, environments change formats and paths, so variance and edge cases turn these flows brittle and high maintenance:
- Rigidity: These flows assume stable fields and params. A new or missing field, a renamed API, or a changed log format can stop the workflow.
- Maintenance overhead: Every source change or product update forces new transforms, tests, and exceptions. This time-consuming maintenance requires deep domain expertise to keep workflows running smoothly.
- Inflexibility with edge cases: Real incidents rarely follow one path. As soon as the case diverges from the template, humans are pulled back into triage, patch the scheme, and restart.
In practice, combining AI with multi-step functional flows takes the best of both worlds while eliminating limitations and shortcomings. AI handles context and correlation; deterministic steps apply changes with checks and approvals. This is the approach Sola takes.
Sola’s agentic workflows for security operations
Sola’s agentic workflows balance heavy duty prompts and rigid playbooks. In simple terms, a single prompt is broken down to multiple logical steps. While AI keeps context and provides flexibility, deterministic steps carry out precise actions through deterministic and validated operations.
Under the hood it is designed as a DAG – Directed Acyclic Graph. Think of it as a clear map of boxes and arrows that only move forward. Each box does one job and passes a small, structured result to the next. That promises avoiding loops and leaves no guessing where things went wrong.
How Sola builds workflows, step by step
Step 1: Breaks a single request into small steps
Sola turns one request into a short sequence of small actions, based on the AI’s security reasoning. In the agentic workflow, outputs of earlier steps become inputs for later steps.
Step 2: Labels steps as logical or functional
Logical steps use AI to interpret, compare, or prioritize in context. Functional steps run exact operations against tools with a fixed schema (API calls, SQL queries, scripts and more), making each result precise and ready for the next step.
Step 3: Orchestrates with guards and previews
Sola’s engine validates every handoff to block mistakes and reduce false positives, while running independent branches in parallel for speed. Each block output is previewed, so a human can inspect, intervene and adjust where needed.
Step 4: Delivers repeatable, auditable runs
Once defined, the same workflow can be reused on demand or scheduled over time to keep investigations up to date, reducing the need to rebuild. This is especially valuable in cybersecurity cases like: ongoing incident tracking, IOC checks and attribution, scheduled intelligence reporting, posture management, or compliance and audits like GCP compliance or an AWS security audit. In the next section, we’ll ground this in a single, real-life security case – the risk of permission drift.
Agentic security workflow in action: excessive permissions
A familiar incident: certain employees accumulate wide permissions across GitHub, Datadog, AWS, Azure, and MongoDB, while some still lack MFA in Okta. As a security operator, you need a daily way to find the riskiest users, nudge them with clear steps, and keep the team informed.
Before: using a one-shot AI prompt
In security terms, this scenario has limitations: Visibility is low because reasoning is opaque and you cannot audit why a user was picked. Results are non-repeatable, so different AI responses can disagree on risk ranking of excessive permissions. Actionability is limited because there is no schedule, no approvals, and no reliable handoff into the systems where work actually happens.
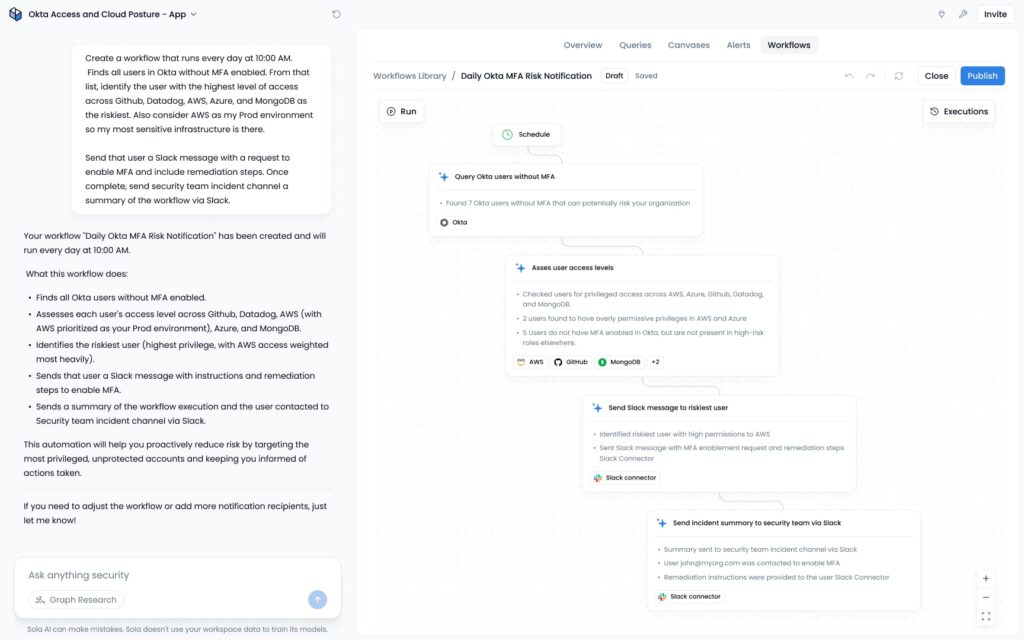
After: using Sola’s agentic workflow
Send that user a Slack message with a request to enable MFA and include remediation steps. Once complete, send security team incident channel a summary of the workflow via Slack.
Each block is inspectable and can be triggered in isolation. The process mixes reliable API and data calls with AI reasoning while validations catch bad shapes early. And because the workflow runs daily at 10am, new drift is caught and turned into consistent action.
Using Sola’s agentic workflow, context moves in order: pull data from Okta, enrich, assess the risk, and then message. The list of Okta users without MFA becomes input for cross-platform permission grading, before an AI step assesses users’ risk level and drafts the MFA request. You can preview the message, add an approval, and the workflow posts a summary to the security channel on Slack.
Discover how to create, manage and run workflows in Sola Docs.
The benefits of agentic workflows
For security operations, Sola’s agentic workflows make investigations and response explainable, safe to run, and easy to adjust. Here is what that means in practice:
Scalability
Complex, multi-step investigations across identity, code, cloud, and SaaS keep moving under load. Sola runs checks across your sources in parallel and remembers and reuses read and transform results for the same inputs, so triage does not slow when volume spikes.
Transparency
Every step shows inputs, outputs, logs, and the exact payloads sent to tools like Slack, Jira, Okta, or GitHub. Execution history records reasons, timestamps, and approvals, so decisions are traceable and audit-ready.
Resilience to change
Work is split into small steps with clear inputs and outputs and strict data checks. Each step validates fields and types. If a log format or vendor API changes, the step fails at that boundary and the bad input does not spread downstream.
Hybrid reasoning
Sola’s AI, with its built-in security reasoning, handles reasoning in context, for example tracing root cause or ranking impact. The workflow then runs concrete steps like API calls and queries to apply the change, so analysis flows into exact action.
Key takeaways for agentic workflows in cybersecurity
AI-only one-shot prompts are inconsistent in complex scenarios, which often occur in security. On the other hand, function-based automations are rigid and require high maintenance. The sweet spot is to guide AI reasoning through structured workflows to ensure intelligent, reliable, and repeatable security operations.
Sola’s way to get there is through its agentic workflows. From a single prompt, Sola breaks down the user’s intent into a sequence of steps, decides which parts need judgment and which are functional blocks, and validates every handoff and shows previews. Since workflows live inside your Sola app, they use your existing integrations. The result is a process you can read, rerun, and adjust.
For security teams and operators, the payoff is clear: It is more accurate because structured checks keep outputs well formed while AI focuses on interpretation, correlation, and security context; transparent because every decision, input, output, and preview is logged end to end; and adaptable because intelligent AI blocks can overcome edge cases independently without breaking the entire workflow.
AI reasoning guided by structure is the practical path forward for security operations: agentic workflows scale, adapt to change, and deliver repeatable results you can trust without the limitations of single-shot prompts or the rigidity of traditional automation tools.
Senior Product Manager, Sola Security
Nadav has a proven track record leading cross-functional teams to build and launch B2B SaaS cybersecurity products. Bridging cybersecurity and AI, he prioritizes trust, measurable impact, and human-in-the-loop guardrails to deliver real value.
