
Not long ago, I spent a year pulling security data across our product infrastructure and development environments, like Kubernetes, CI/CD, and our cloud accounts. I parsed logs by hand, wrote scripts, and funneled everything into a SIEM. It was brutal but necessary at the time. It taught me plenty.
But that was the reality of cybersecurity before AI.
Fast forward to the present, and the landscape has transformed dramatically. The cultural shift with the emergence of AI is real, and it’s not just about slapping some new tech on old problems; it’s about redefining the way security teams operate.
The cultural impact of AI adoption
Whether you like it or not, AI is creating seismic shifts everywhere, and cybersecurity should be no exception. The traditional “chase the next alert” habit is giving way to a more proactive “ask → answer → act” approach. This isn’t just about adopting new technology; it’s about fundamentally changing how security teams work, and how humans stop being the glue between tools.
The cultural tax of maintaining the status quo is becoming unsustainable. Teams are drowning in alerts, wasting precious time stitching together data from disparate sources, and struggling to keep up with the volume, velocity, and variety of modern security threats. The result is a culture of heroics, where security teams are constantly firefighting, rather than proactively securing their environments.
AI adoption is resetting expectations around two critical aspects: fast, explainable answers and safe automation embedded where work already happens. It’s about moving from a reactive stance to one that’s proactive and efficient. By automating tasks like enrichment, scoring, and first-pass prioritization, humans can focus on higher-level judgment calls, approvals, and actions.
This cultural shift isn’t just about technology; it’s about changing the fabric of how security operates. It’s about creating habits rather than relying on heroics, and about making security a collaborative effort rather than a siloed function.
Old school security: What’s holding us back
Traditional security practices have been the backbone of the industry, emphasizing discipline, repeatability, and human oversight. It deserves credit and is still useful. But at today’s scale of SaaS sprawl, cloud accounts, identities, and “shadow” everything, it stalls. Every tool speaks a different dialect, so people become the glue: hopping consoles, exporting CSVs, reconciling owners, and begging other teams for context.
That glue work has a cost you can measure. TTFA (Time to First Answer) drifts from minutes to days. MTTR (Mean Time to Recovery) bloats as tickets bounce around. False-positive rate climbs because you ship noise to humans. Coverage drift grows as the stack changes faster than your checks. Meanwhile, simple questions turn into mini-projects and the real incidents slip through while you’re busy “managing the process.” This is where security turns into a disabler: slow, ticket driven, and risk averse when the business needs speed.
The job isn’t to stare at screens and escalate forever. It’s to ask a clear question, get an explainable answer, and run a governed change, with receipts. Keep the discipline; lose the manual glue. Put humans on judgment and approvals, not on copy-paste and context hunting. That’s the exit from perpetual triage.
Embracing the AI-first operating model
AI is not a magic solution; build small, typed steps you can trust, then chain them.
Security roles are evolving to accommodate this new approach. Analysts now own top questions and the query library, writing evidence summaries and focusing on metrics like TTFA and false-positive rates. Detection/Response Engineers design small, typed steps and set approvals and rollbacks, measuring the percentage of governed automation and change failure rates. SecOps Leads own guardrails and SLOs, tracking MTTR and coverage drift.
These evolving roles come together to support a cohesive AI-first lifecycle. The process is integrated, with each step building on the previous one to create a continuous loop of improvement.
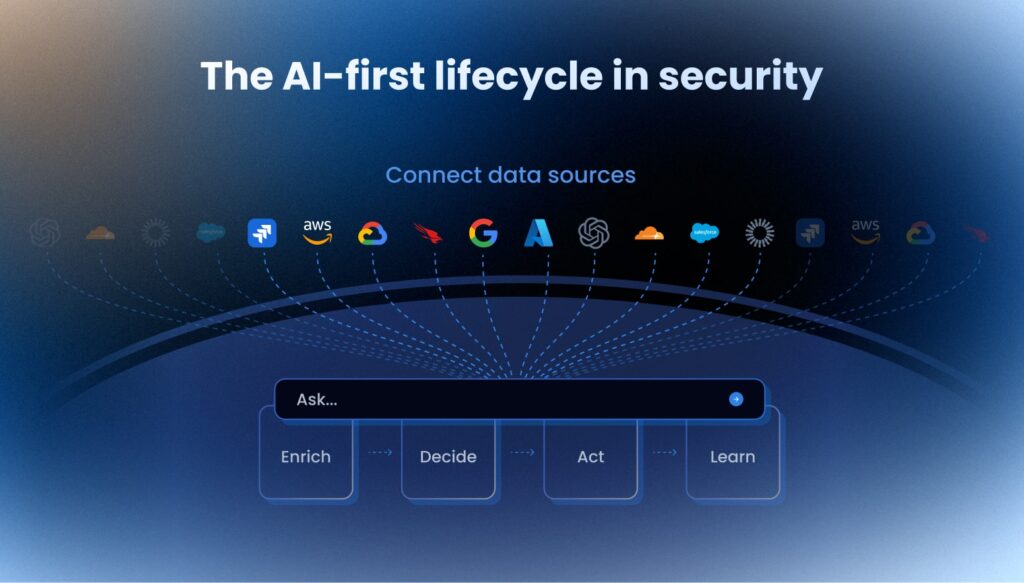
The AI-first lifecycle is a five-step process that transforms how security teams work:
- Connect: Core sources (like Okta, AWS, and GitHub) are connected, with identities deduplicated.
- Ask: Questions are saved as reusable queries, making it easier to get answers across different sources.
- Enrich: Findings are enriched with security context like owner, exposure, and criticality, using baked-in security knowledge.
- Decide: Actions are decided based on scoring, ownership, and approval tiers.
- Act & Learn: Actions are previewed, approved, executed, verified, and rolled back if necessary, with continuous tracking of TTFA and MTTR.
How the new culture of security actually changes
Security moves from chasing alerts to asking clear questions, getting explainable answers, and acting with receipts.
One key shift is from console-driven to question-driven approaches. With an AI platform for cybersecurity like Sola, a single question pulls in business context (owner, criticality, customer impact) and product infrastructure data (cloud, CI/CD, and more) to return an explainable, repeatable answer with receipts, cutting the time spent on manual context building.
Another shift is from tickets and handoffs to in-flow, governed workflows. Answers route directly to the owner, with preview, approval, action, verification, and rollback all happening in one flow, reducing stalls and making changes safer.This is the flip from a disabler to an enabler: the right owner gets the answer and the approval to act where they work, so work moves.
The cultural shift also moves security teams from reactive triage to proactive drift checks. Lightweight, scheduled drift detectors notify owners with evidence so issues are fixed before they page you. That reduces false positives and avoids war rooms.
These changes are not about technology alone. They build a culture of visibility, automation, and accountable ownership. Measure TTFA, MTTR, false-positive rate, and coverage drift. Adopt AI-first workflows. Buy back time and focus on real problems so you can ship real improvements.
The AI-first era in security: Benefits and risks
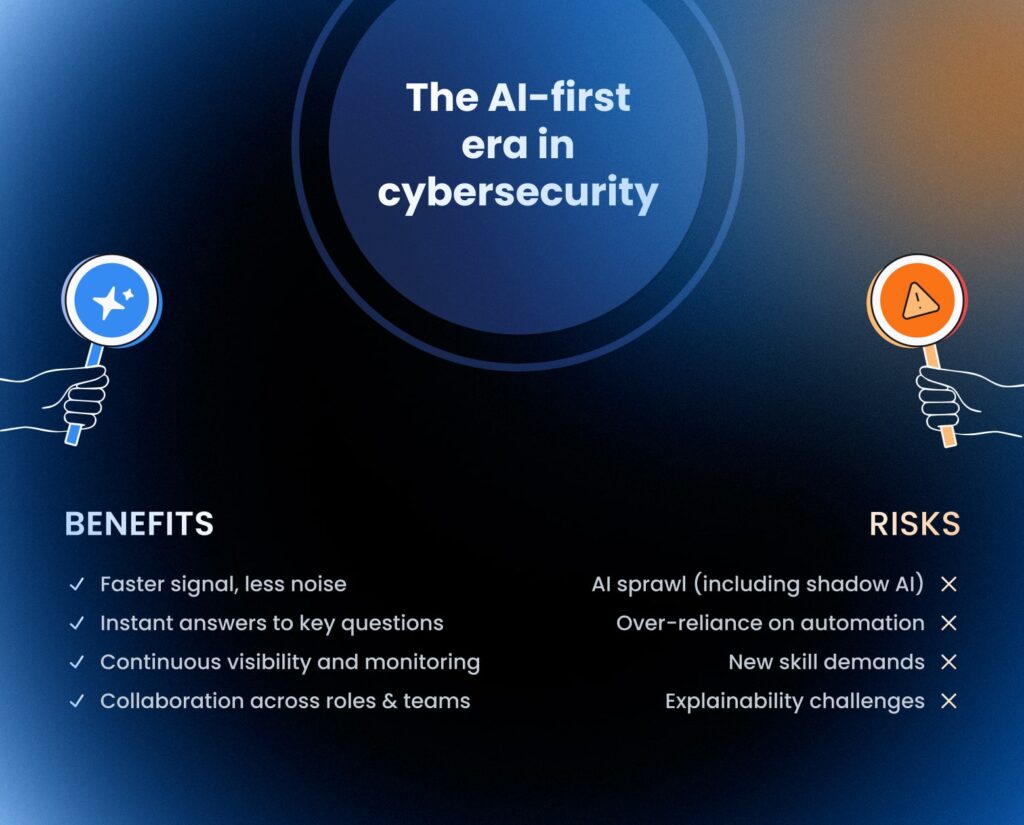
So, now that we stopped chasing alerts and started asking smarter questions, we need to also be aware of the tradeoffs associated with this new era in security. We’ll start by highlighting the benefits:
- Speed and signal. Automation clears noise so humans focus on judgment. Continuous monitoring across cloud, SaaS, endpoints, and infrastructure stops spreadsheet theater.
- Instant answers. Teams query data directly without dependency bottlenecks and get explainable, citable results they can rerun.
- Continuous visibility. Always-on checks catch drift early and feed improvements back into rules and models.
- Collaboration in the flow. Security lives inside DevOps, R&D and IT workflows, not in tickets that bounce between teams. In Sola, that looks like Queries, Workflows with approvals, and shareable evidence packs.
That is the upside, but there are risks involved as well. Here are some of the tradeoffs, plus the guardrails that keep them contained:
- AI sprawl. Shadow tools and models appear without oversight. Mitigate with identity-mapped approvals, a central catalog of queries and workflows, and receipts for every change.
- Over-reliance on automation. Blind spots and false confidence are real. Use approval tiers, blast-radius checks, preview by default, post-change verification, and safe rollbacks.
- New skill demands. Data plumbing, governance, and automation design are required. Keep steps small, typed, and testable; run lightweight evaluations; pair Security with Platform Engineering.
- Explainability. Audits expect “why.” Prefer feature-based scoring and attach evidence packs to every answer and change.
Key takeaways: Accelerating the cultural shift
The cultural shift to AI-first security is about transforming how security teams work, not just adopting new technology. To make the shift real, prove its value for your security setup and keep risk in check:
- Start small. Connect the likes of Okta, GitHub, and AWS. Come up with the questions you care about most, map owners – and save your top questions as reusable queries.
- Use governed workflows. Preview by default, apply approval tiers, execute, verify, and keep rollback ready. Begin with low-risk fixes and require approvals for high-impact changes.
- Measure outcomes weekly. Track TTFA, MTTR, false-positive rate, and coverage drift. Improve one step at a time.
- Build the culture. Prioritize visibility, automation, and accountable ownership. Put decisions with people and let machines fetch, enrich, and prep inside DevOps, IT and business workflows.
By following these steps, security teams can buy back time and sanity, focusing on real problems and shipping real improvements, ultimately building a security culture that pairs discipline with AI-powered adaptability.
Head of Security Innovation, Sola Security
Idan lives where security meets invention, after years shaping cloud and DevSecOps at Fiverr, AppsFlyer, and Verint. As Head of Security Innovation, and a proud Sola power user, he puts AI to work on the noisy bits so humans keep the judgment calls.
