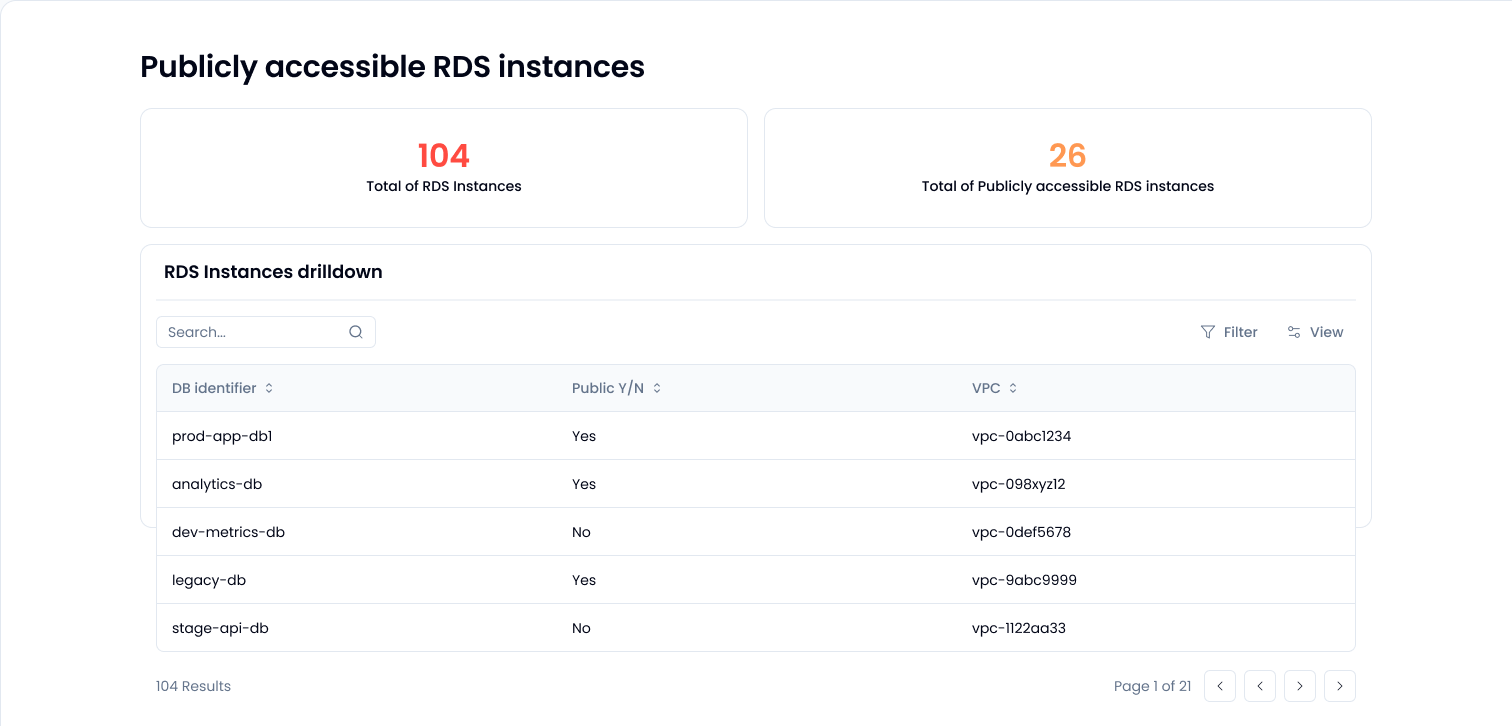
If it’s set to public and in a public subnet? Yes.
PubliclyAccessible flag is set to true and the instance lives in a subnet with internet access. That’s the magic combo. If either one is false, it’s not exposed.You can find this out the hard way, by clicking through the AWS console. Alternatively, you can just ask the question in a Sola app and get the answer instantly. Whether you use our prebuilt AWS compliance app or roll your own with the AI copilot, it takes minutes.
Sola apps that could help you
Visit the App GalleryRDS public access: understanding the risks
When RDS public access is enabled, your database is reachable over the internet—great for testing, disastrous for production. This isn’t just bad practice; it’s a compliance red flag, and in some industries, it’s a full-blown violation.
AWS itself doesn’t prevent you from misconfiguring public access. It gives you the tools (like VPC settings, subnet visibility, security groups, and NACLs), but it’s entirely on you to get them right. A common misconception is that setting PubliclyAccessible=true is enough. It is not. Your database also needs to be in a public subnet, with open security group rules and an internet gateway.
How to check RDS public access – and how to lock it down
Start with these basics:
- In the RDS console or via CLI, check
PubliclyAccessiblestatus. - Audit the VPC subnet’s route tables and see if it routes through an Internet Gateway.
- Confirm that security groups don’t allow unrestricted ingress (e.g.,
0.0.0.0/0on port 5432 or 3306).
For a real-world-ready solution, use a tool like Sola to continuously check that no RDS instance gets deployed publicly without a reason – and without someone knowing. Alternatively, you can just use AWS Config.
Best practices for AWS network security and compliance
When RDS public access is enabled, your database is reachable over the internet – which is great for testing, but disastrous for production. This isn’t just bad practice; it’s a compliance red flag, and in some industries, it’s a full-blown violation.
AWS itself doesn’t prevent you from misconfiguring public access. It gives you the tools (like VPC settings, subnet visibility, security groups, and NACLs), but it’s entirely on you to get them right. A common misconception is that setting PubliclyAccessible=true is enough. It is not. Your database also needs to be in a public subnet, with open security group rules and an internet gateway.
- Default to private: Unless there’s a very specific reason, databases should live in private subnets.
- Use VPC peering or VPNs: Internal apps should connect via private routes.
- Automate checks: Sola makes it dead easy to run checks on RDS configurations and alert if something drifts.
This problem isn’t limited to RDS. The same applies to services like API Gateway, where exposure risks come from lax resource policies and public routes. To secure AWS API Gateway, you need to combine route protection with private integrations and endpoint restrictions.
Another critical piece: the VPC endpoint policy. Just because traffic stays inside your VPC doesn’t mean it’s safe. If you’re using endpoints to access S3, Secrets Manager, or anything else, make sure you’ve actually scoped who can use them.
Summary
If you’ve got cloud infrastructure running and no idea how it’s configured, you can fix that with Sola: use our AI co-pilot to create your app, ask about your RDS instance’s status, connect your AWS data, and get your answer in minutes, not days.