TL;DR
Require authentication: Use IAM, Cognito, or Lambda authorizers. No public endpoints unless absolutely needed.
Throttle traffic: Set rate limits and quotas per method or client.
Log and monitor: Enable CloudWatch and X-Ray. Track what’s exposed and what’s being hit.
Add WAF to block known attacks. Run AWS Inspector and regular AWS security audits to catch what you missed.
And with Sola, you can build your own AWS API Gateway security app that checks real data from your environment.
Secure AWS API Gateway in Three Moves
Require authentication: Use IAM, Cognito, or Lambda authorizers. No public endpoints unless absolutely needed.
Throttle traffic: Set rate limits and quotas per method or client.
Log and monitor: Enable CloudWatch and X-Ray. Track what’s exposed and what’s being hit.
Add WAF to block known attacks. Run AWS Inspector and regular AWS security audits to catch what you missed.
And with Sola, you can build your own AWS API Gateway security app that checks real data from your environment.
Sola apps that could help you
Visit the App GalleryWant to know which APIs are actually unsecured?
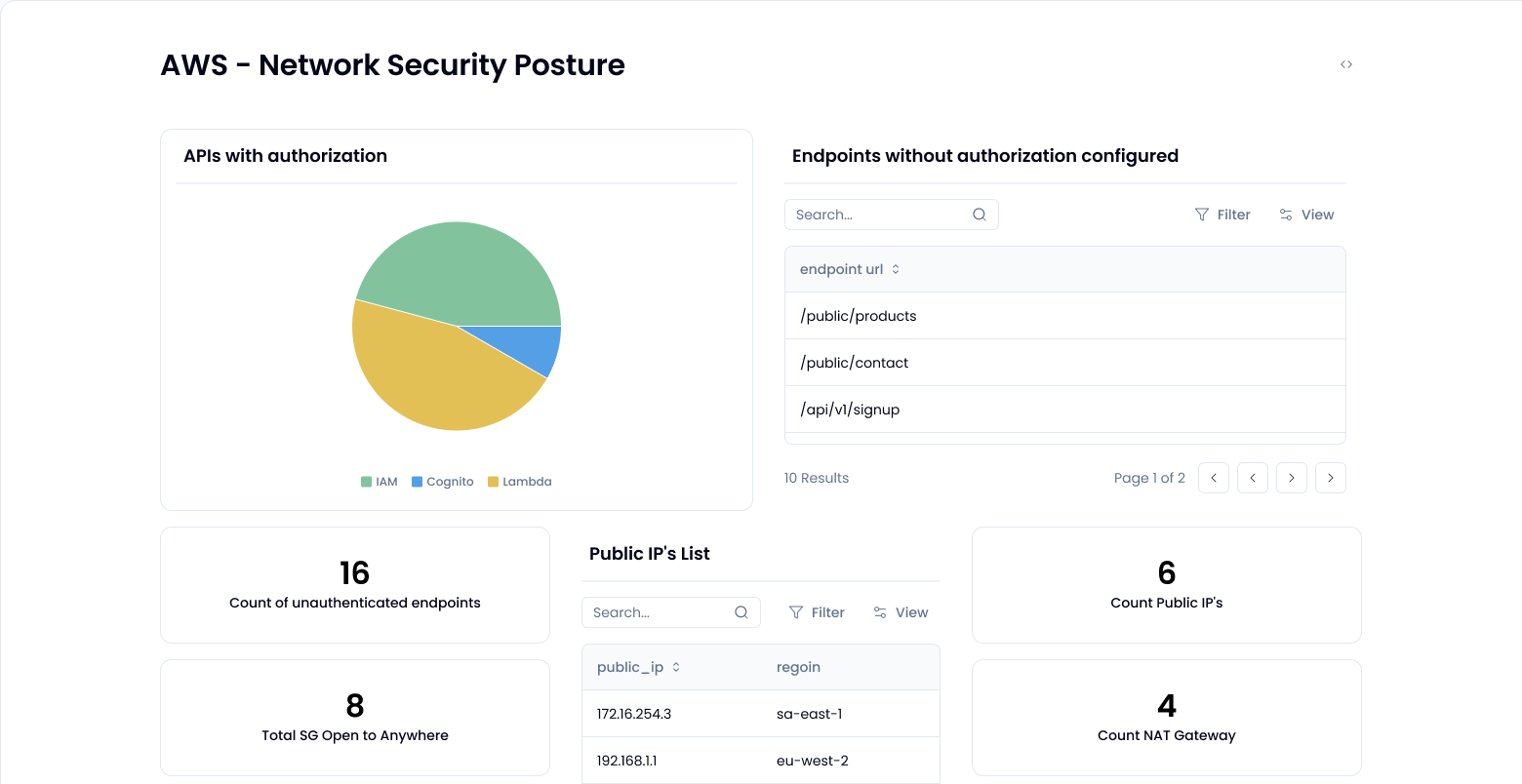
Most teams think their API Gateway is locked down, until someone runs a check and finds unauthenticated endpoints open to the internet. Securing AWS API Gateway isn’t just about setting policies; it’s about knowing what’s actually live, what’s exposed, and what’s misconfigured.
You need answers to questions like:
- Which endpoints are public and unauthenticated?
- Are rate limits and throttling really in place?
- What methods are exposed without protection?
Connect your cloud account to Sola, define these questions, and instantly surface the answers. No code, no guesswork.
AWS Security Best Practices for API Gateway
- Auth Everything: IAM for internal access, Cognito or JWTs for users, custom authorizers if needed. No public APIs unless they’re read-only and harmless.
- Throttle by Default: Set sensible limits to avoid DDoS-by-misuse. Even trusted clients mess up.
- Log All Requests: Use CloudWatch Logs and AWS X-Ray. It’s your only trail when things go sideways.
- Attach WAF: Protect against injection attacks, bots, and other low-effort exploit attempts.
- Audit Frequently: Use AWS Inspector and IAM Access Analyzer. If you’re not auditing, you’re guessing.
Implementation Tips That Matter
- Use Resource Policies: Limit access by IP, VPC, or region.
- Lock Down Stages: Don’t let dev or test APIs live publicly.
- Clean Up: Remove unused APIs, keys, and stale endpoints regularly.
- Tag Everything: Helps in audits, cleanups, and figuring out what’s actually in use.