Use GCP audit logs to meet compliance goals, without drowning in complexity
And that’s where most teams get stuck: buried under a mountain of logs with zero clarity. Enter Sola. With the GCP Compliance app, you can install, plug in your GCP data source, and instantly get answers to the questions auditors care about, such as who accessed what, when, and why. Or better yet, build your own logic using AI if off-the-shelf isn’t your thing.
Sola apps that could help you
Visit the App GalleryBest practices for monitoring GCP audit logs
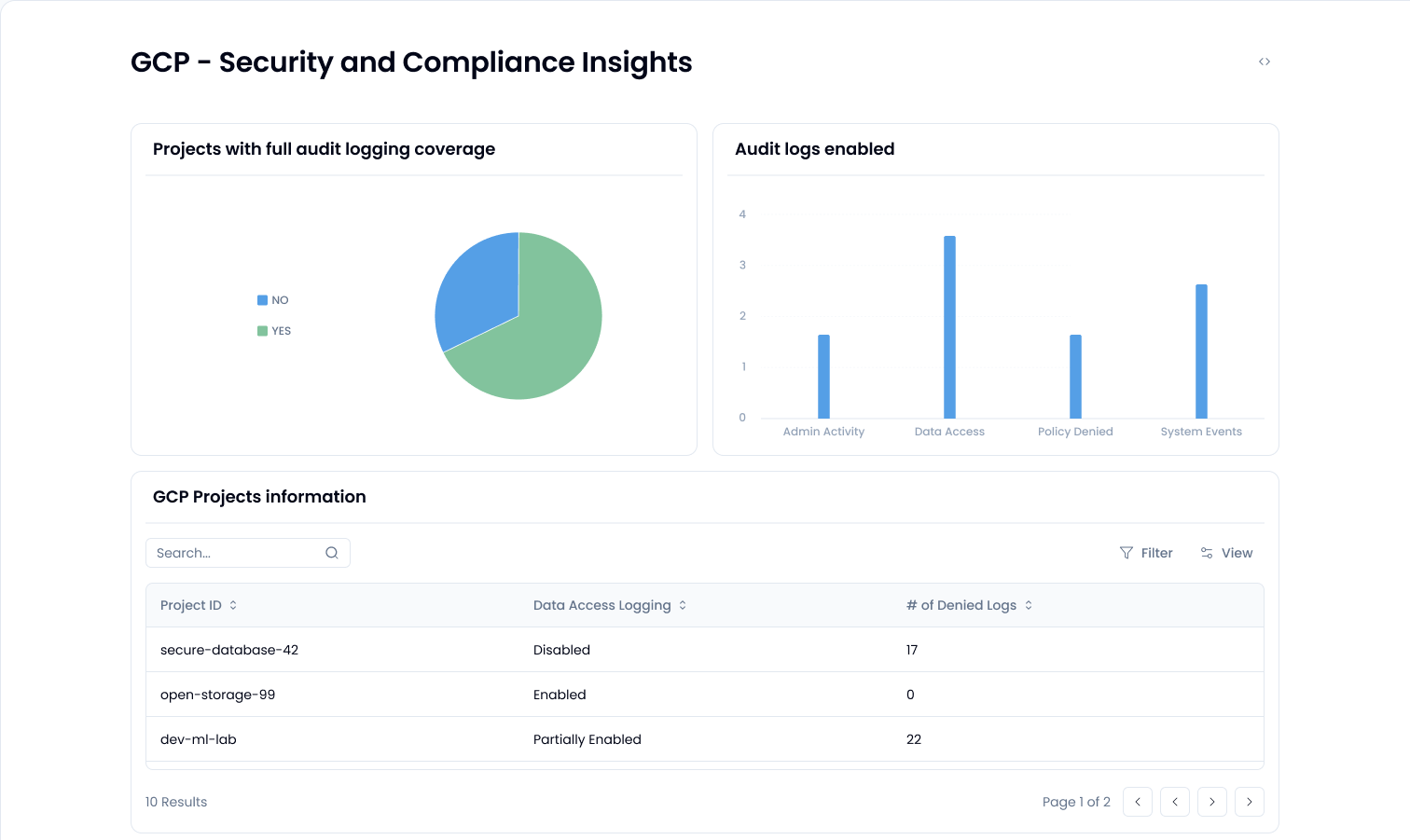
GCP audit logs are split into three types: Admin Activity, Data Access, and System Event logs. For cloud security compliance, you need visibility across all of them. Here’s how to do it right:
- Enable all audit log types: By default, only Admin Activity logs are enabled. You’ll need to explicitly turn on Data Access logs, especially for tracking read operations on sensitive data.
- Use Log Sinks to centralize: Route logs to Cloud Logging, BigQuery, or external SIEMs. Without a centralized logging strategy, your chances of passing a compliance audit? Slim.
- Set up meaningful alerts: No, not every API call needs an alert. But access to a sensitive resource outside of working hours? Absolutely.
With Sola, you can define these questions directly in your workspace. “Alert me if a new service account is created with owner privileges.” Done. You don’t need to reverse-engineer compliance from scratch.
Implementation strategies that won’t burn cycles
Getting from log collection to GCP security insights requires more than dumping logs into BigQuery. Start with:
- Pre-built dashboards: GCP provides basic visibility, but they aren’t tailored to compliance needs. You’ll want to customize them, or just use a Sola app that already does.
- Retention policies: Most audit logs are retained for 30 days. If you’re targeting GCP SOC 2 compliance, configure longer retention in Cloud Logging or export to storage buckets.
- Access control: Only specific roles should access logs. Use IAM to lock it down and monitor who views what.
Cut the noise, monitor what matters
Compliance doesn’t wait for perfect setups. With Sola, you can build your own app that cut straight to the point, like who’s accessing sensitive resources or misconfiguring IAM roles. Want to tweak alerts? Visualize anomalies? You’re not at the mercy of your SIEM team anymore.
Answer more security questions
Cyber security for startups: Where to Start?
How to check GitHub repo branch protection?