Find and fix overly permissive NSG rules
With Sola, you can build an app that pulls a full inventory of your Azure network security groups, flags high-risk or overly permissive rules, and tracks changes to security group configurations over time, across subscriptions and environments.
Sola apps that could help you
Visit the App GalleryHow to find overly permissive Azure NSG rules
1. Filter for “Allow” rules with 0.0.0.0/0
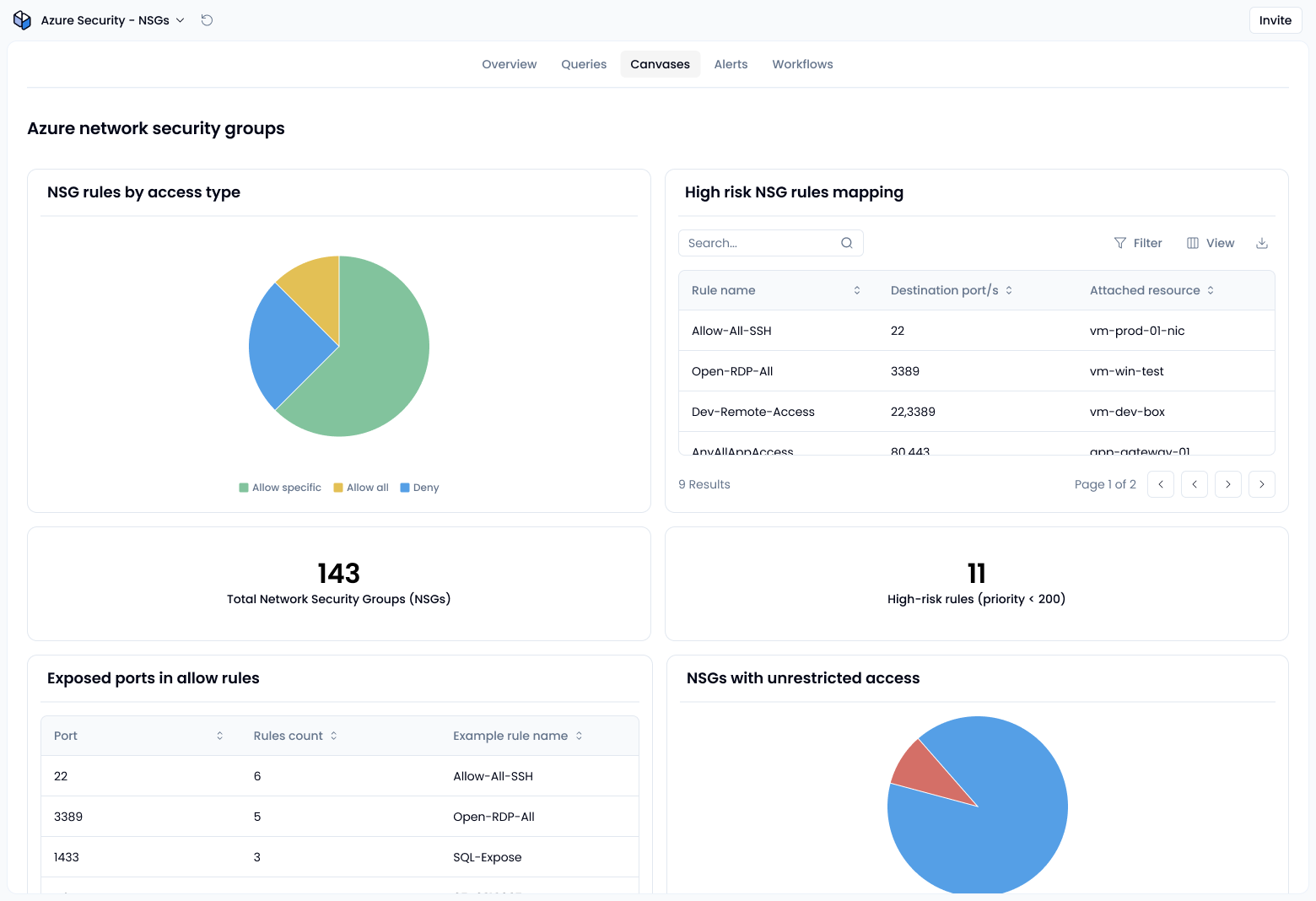
Any rule that allows inbound access from all IP addresses (0.0.0.0/0) deserves extra scrutiny, especially when applied to critical services. Combine that with destination port ranges like * or common ports (22, 3389, 1433), and you’ve likely got an exposure risk.
2. Review NSG priority and rule conflicts
Azure NSG priority determines which rule gets enforced. Lower numbers take precedence. That means a broad allow rule with a priority of 100 overrides a deny rule set at 300. Check for misordered or conflicting rules that unintentionally open access.
3. Map rules to actual resources
Once your NSG rules are configured and visible, it’s important to understand where they’re actually applied. Tie each Azure security group to the subnet or VM it’s protecting, so you understand the real impact. Pay attention to Azure application security groups if you’re segmenting by workload type.
How misconfigured NSGs quietly expose your Azure environment
A network security group (NSG) in Azure is a firewall that controls inbound and outbound traffic at the subnet or NIC level. It works by applying NSG rules. Each rule defines access based on IP ranges, ports, and protocols, with a priority value determining which rules win when conflicts exist.
But just “having audit logging enabled” isn’t enough. Logs need to be correctly routed, stored, and retained long enough to support investigations or compliance checks. This is where most setups fall short.
Monitor Azure network security with Sola
Sola helps you build a tailored app that shows you exactly where NSGs are misconfigured, what rules are too open, and which resources are exposed. Simply ask Sola’s AI assistant to identify overly permissive NGS rules in your Azure environment and you’ll be able to set up an app, based on your data.
You can also set up alerts to track changes to NSG configurations and enforce best practices across all environments.
Answer more security questions
How to check Azure managed identity assignments
How to monitor security risks across cloud accounts?
How to audit file sharing across Google Workspace?