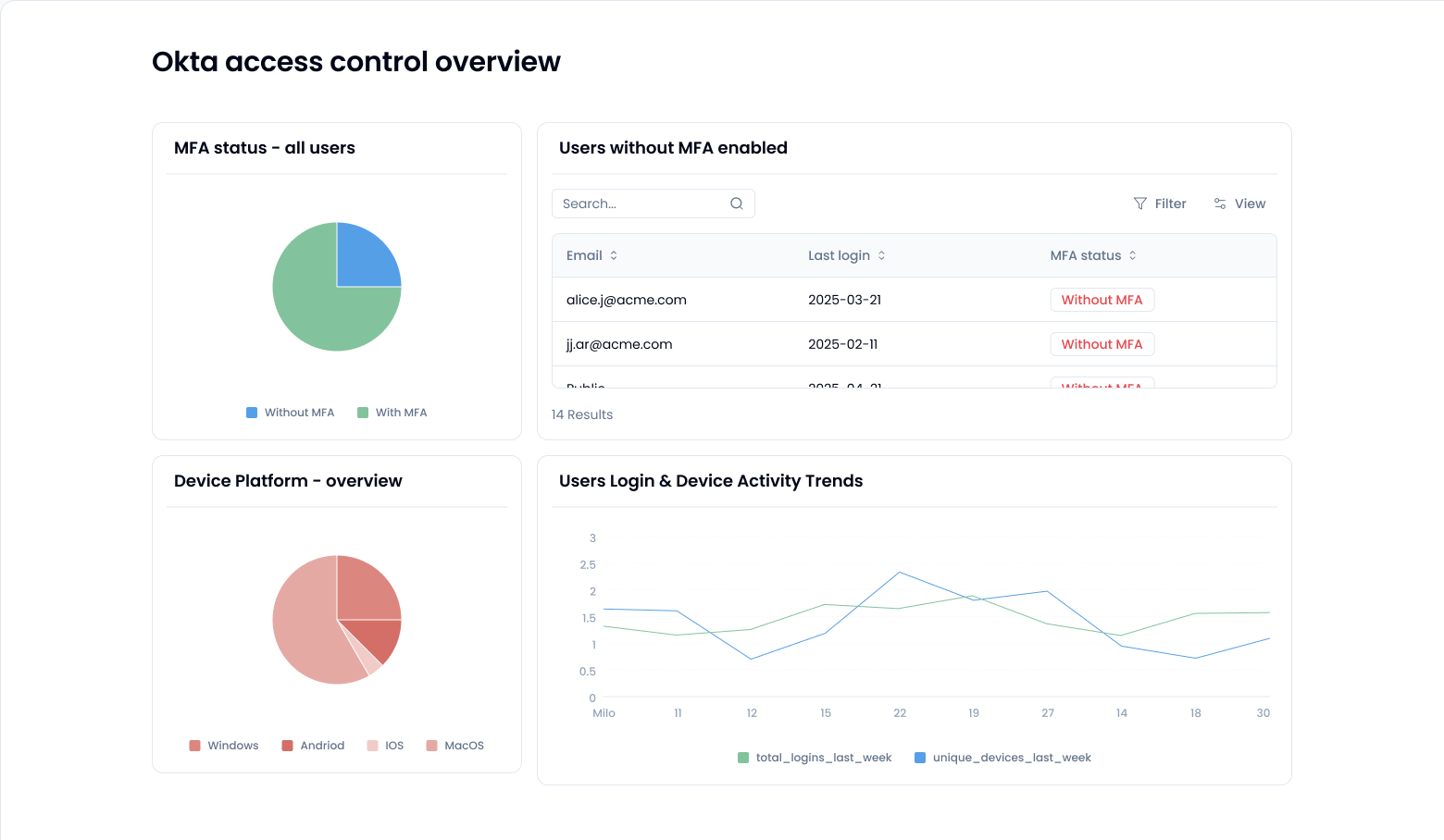
Use Okta reports or API to find users without MFA
Most folks assume Okta just handles MFA out of the box and that once a policy is in place, everyone complies. Not quite. Even with a policy in place, enrollment is only as good as its enforcement. That’s where you (or your super admin) come in. You need to see who’s actually enrolled, who’s ignoring it, and who’s somewhere in limbo.
Sola apps that could help you
Visit the App GalleryInstead of drowning in audit logs or clicking endlessly in the admin console, just build your own view with Sola’s Access Control Okta Insights app. Plug in your Okta instance, define your question like “show me all users who haven’t enrolled in MFA” using our AI agent, and the answer is right there. You can even customize it further to get more clarity.
Understand your Okta user list and permissions
Okta’s user management model gives super admins the power to view MFA enrollment across all users, but you need to know where to look. You can start from the Admin Console under Reports > Authentication > MFA Enrollment. Here, you can export a list showing who’s in and who’s out.
Want to go deeper? Use Okta’s API (/api/v1/users) to fetch the Okta user list, then correlate it with the factor enrollment endpoint (/api/v1/users/${userId}/factors). This lets you programmatically sift out users without any enrolled factor.
Pro tip: Watch out for users with no assigned apps. They often fall through the cracks when enforcing MFA. And remember: not all admins are created equal. You need super admin permissions to see the full picture.
Implementation tips: Don’t just enforce, monitor
Enforcing MFA isn’t a one-time deal. People leave, roles change, new apps get added. Make sure your process includes regular reviews of MFA status, especially for privileged users. Automate it if you can (hint: Sola can help).
Integrate checks into your access management flow. Before granting new permissions or app access, validate MFA enrollment. You can even turn it into a trigger for alerts or conditional access policies.
Answer more security questions
Cybersecurity for startups: Where to Start?
How to monitor GCP audit logs for compliance?
How to check GitHub repo branch protection?