Track files, logins, and app access
Detecting external access isn’t a one-time task. It’s a continuous battle against link oversharing, unnoticed logins, and app permissions no one remembers approving.Google’s native tools do give you dashboards and search capabilities for tracking file sharing, logins, and app access. The problem is they’re spread across different consoles, built more for IT reporting than fast security answers, and usually mean sifting through logs or building custom filters. That’s where Sola cuts the grunt work: ask in plain English and get straight to the answers , like Which external users still have access to confidential files? or What apps have risky scopes?
Sola apps that could help you
Visit the App GalleryAudit external file sharing
The most obvious way data walks out the door? Shared Drive links. You need to:
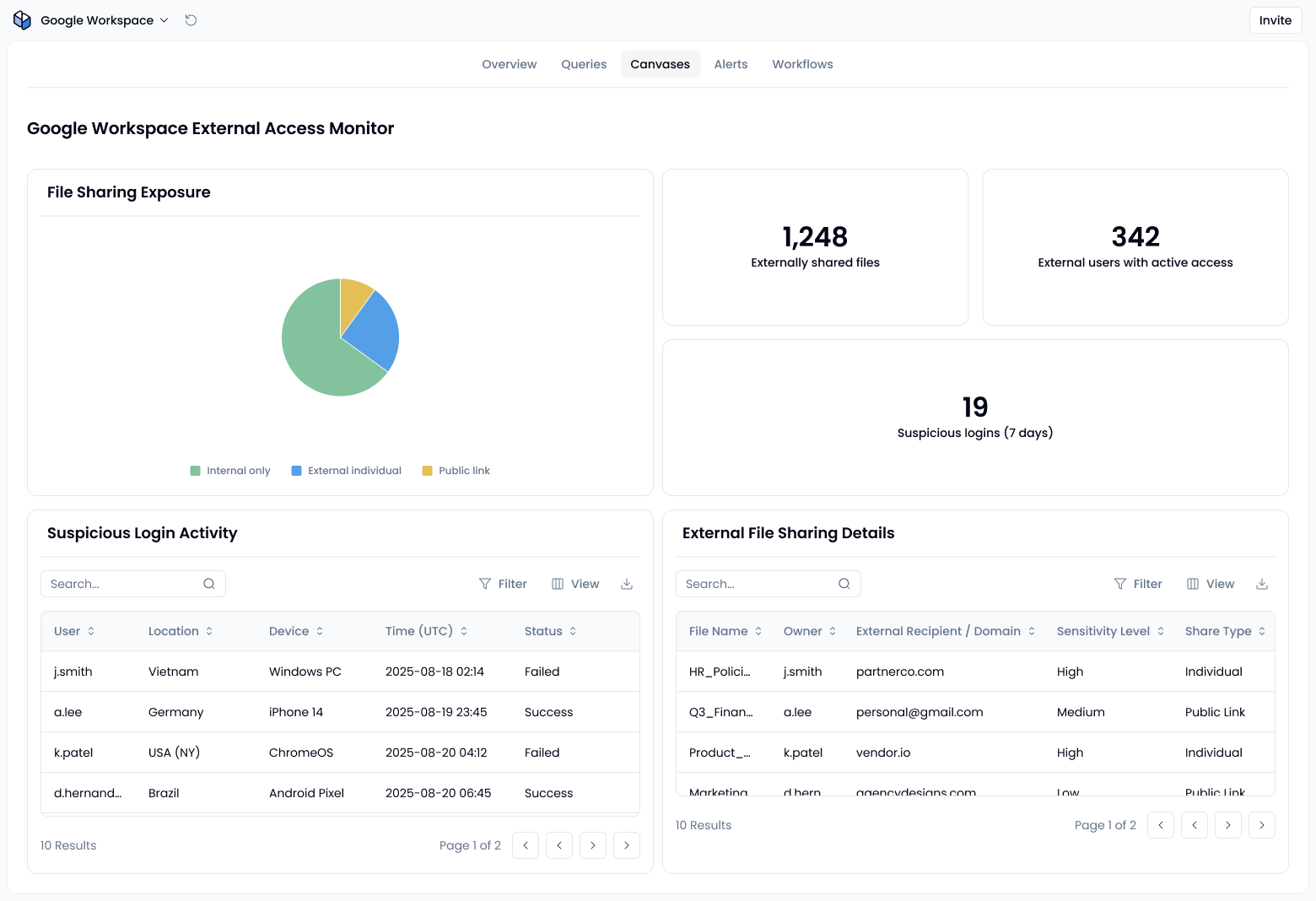
- External File Sharing: Security Center File Exposure Report + Investigation Tool.
- Login Monitoring: Login audit logs (Admin console / Cloud Logging).
- App Access Review → OAuth Token audit logs + Admin console app access controls.
Sola’s Google Workspace security and access insights app includes prebuilt queries that give you all of that in a single dashboard, broken down by file sensitivity, share type (individual vs public), and user. You can also create alerts like confidential files shared externally or unsharing dropped significantly this week to flag unusual behavior.
Monitor suspicious login activity
Login attempts from outside known locations or new devices should raise eyebrows. Look for failed or suspicious login events, and consider defining filters for unusual IP geolocation or odd time-of-day activity in your own dashboards or SIEM.
With Sola, you can find this data if you download the aforementioned Google Workspace app. You can also just ask the AI: Show all logins to user X from unrecognized devices or Map unusual login patterns by country. No manual log combing required.
Review third-party app access
Third-party apps with OAuth access are another backdoor. Here’s what to watch:
- Which apps are connected
- Who authorized them
- What permissions they requested
Sola lists connected apps by scope, shows who enabled them, and lets you filter for high-risk scopes (like Drive read/write). You can even trigger alerts for newly authorized apps or admin-level grants.
Whether you want a ready-to-go security app or just need to ask one-off questions about Google Workspace security, Sola’s got you covered. Build your own app from a question like “Which files are exposed externally right now?”, or let the AI generate a live chart, query, or alert for you.
Answer more security questions
How can I inventory shared Drive files that contain sensitive data?
How to audit file sharing across Google Workspace?
Cyber security for startups: Where to Start?