Use GitHub settings or automate it with a security tool
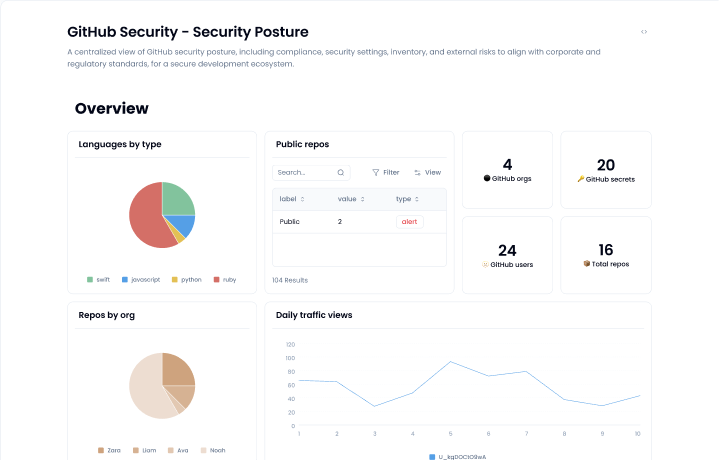
Manual checks are fine if you’ve got one lonely repo. But if you’re aiming for real GitHub security, you need to know which branches are protected, which aren’t, and what rules are being enforced across all your repos. That’s where Sola comes in. You can spin up a custom app with our AI co-pilot or grab the GitHub Security Posture App from the gallery. Either way, you’ll get instant answers without messing around with integrations or configs.
Sola apps that could help you
Visit the App GalleryBest Practices for GitHub Branch Protection
GitHub branch protection rules are your front line of defense. At a minimum, you should enforce:
- Required pull request reviews before merging.
- Status checks to ensure tests pass.
- Push restrictions to prevent direct commits to protected branches.
- Required signed commits for auditability.
- No force pushes or deletions on main/release branches.
That’s your GitHub compliance starter pack right there. These settings block most of the stupid mistakes that turn into production incidents or security audits from hell. If you’re not enforcing these org-wide, you’re probably flying blind.
How to Check Branch Protection at Scale
For one-off checks, go to your repo on GitHub, then:
- Click Settings → Branches
- Under “Branch protection rules”, select the branch
- Review the applied settings (pull reviews, checks, etc.)
For multiple repos, the GitHub REST API (/repos/{owner}/{repo}/branches/{branch}/protection) is your friend. Or just skip the scripts and use Sola: build an app that shows protection status across all branches and repos, flags violations, and lets you take action without leaving your workspace.
With the GitHub Security Posture App, you can monitor protection status across all branches and repos, flag gaps, and even create alerts. Customize it however you like. Yes, even your weird branching strategy.
Beyond branch protection: Additional blind spots
Branch protection alone won’t save you if the rest of your pipeline is unsecured. Many teams enforce strict rules on main but leave staging or feature branches wide open, which means risky changes can still find their way into production. Even worse, some deployments might bypass protected branches entirely. Even worse, deployments might bypass protected branches entirely.
Even worse, deployments might bypass protected branches entirely. If you’re using GitHub Actions deployments, make sure they’re only triggered from branches that meet your protection standards and pass all required checks. Otherwise, you’re just opening the side door.
Another blind spot is secrets in code. It’s still common to find GitHub API tokens hardcoded in commit history or accidentally pushed to public forks. Branch protection won’t catch that. You need scanning in place to detect token exposure before it becomes a security incident.
So yes, lock down your branches. But also consider the full picture: how code is merged, how it’s deployed, and what might be exposed in the process. GitHub gives you the controls. Sola uses AI to help you make sense of them by surfacing risks, gaps, and blind spots across your workflow.
Answer more security questions
How to find dismissed Dependabot alerts on GitHub
How to check GitHub repo branch protection?
How to monitor GitHub production deployments?