Review audit status and fix misconfigurations
With Sola, you can create an app that automatically lists your databases, flags missing or misconfigured audit settings, and alerts you to gaps or high-volume anomalies across your Azure environment.
Sola apps that could help you
Visit the App GalleryHow to verify Azure audit logs properly
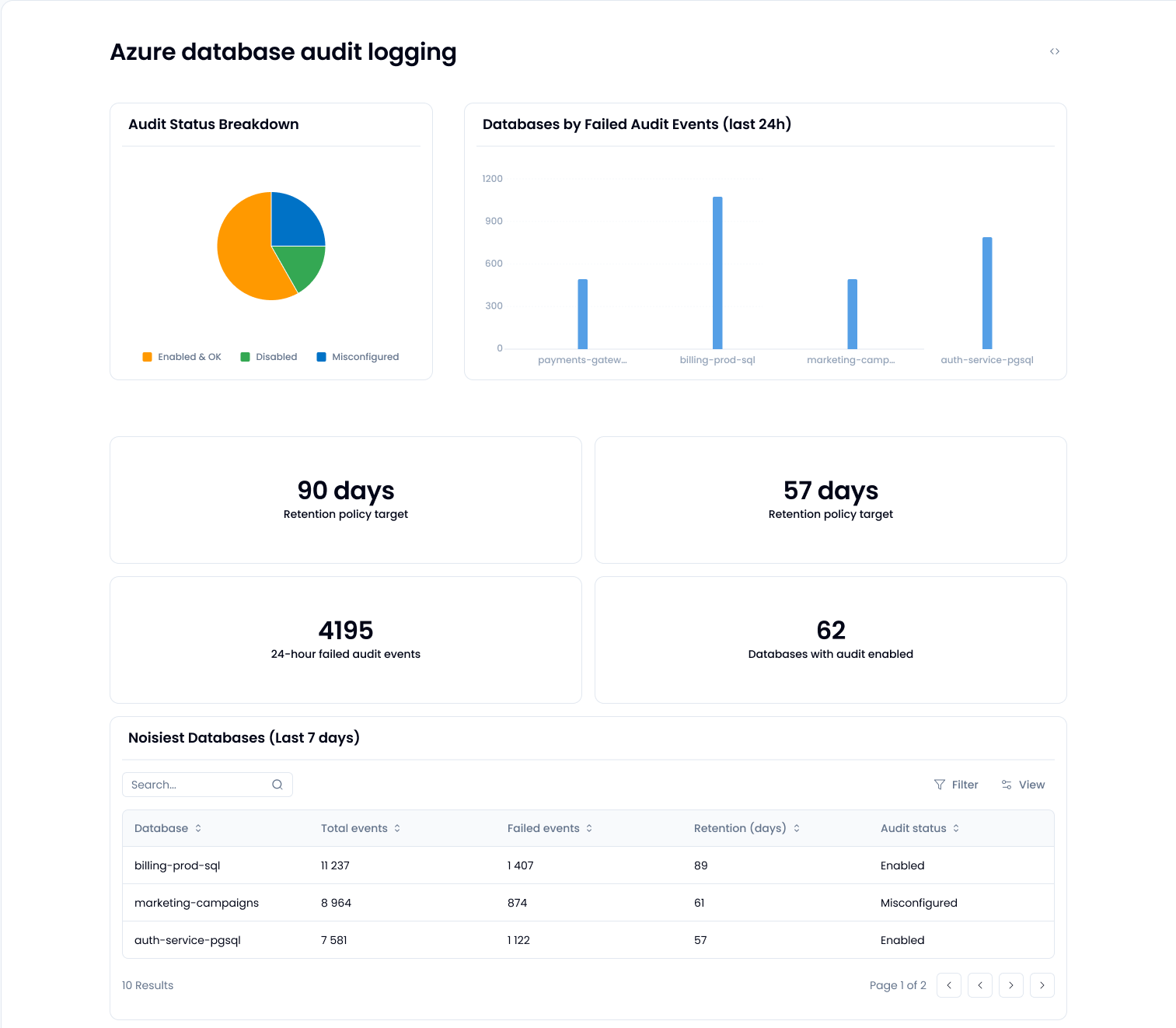
1. List all database instances and their audit status
Start by pulling a full inventory of Azure SQL, PostgreSQL, and MySQL databases. For each, confirm whether audit logging is enabled and where the logs are being sent (e.g., Log Analytics, Storage Account, Event Hubs).
Sola makes this easier by automatically surfacing all database instances and showing whether their audit config is active, missing, or incomplete.
2. Check for misconfigurations and missing logs
Look for gaps like:
- Audit logging enabled but no destination configured.
- Policies only auditing successful operations, ignoring failures.
- Logs missing for certain dates or completely absent for specific databases.
These misconfigurations create blind spots—especially dangerous when they go unnoticed.
3. Review retention and analyze audit volume
Logs kept for only 7 or 30 days won’t help much during an incident investigation. Flag any database with retention under 90 days. Also, track audit event volume to identify unusually noisy or suspicious databases. Your top 10 by event count is a good place to start.
Why Azure auditing matters
Audit logs are the bare minimum when it comes to visibility. Without proper Azure auditing, you have no way to prove (or detect) what’s happening in your databases. Whether it’s unauthorized queries, privilege abuse, or config changes, your audit trail is often your only record.
But just “having audit logging enabled” isn’t enough. Logs need to be correctly routed, stored, and retained long enough to support investigations or compliance checks. This is where most setups fall short.
Make Azure auditing work with Sola
With Sola, you can build an app that continuously checks your audit logging posture. From missing logs to incomplete settings, everything is tracked in one view. You can also create alerts, automate reviews, and stay ahead of compliance issues – no manual checks required.
Answer more security questions
How to check Azure managed identity assignments
How to monitor security risks across cloud accounts?
How to audit file sharing across Google Workspace?