Trace inherited GCP IAM roles across the hierarchy
With Sola, you can use our AI assistant to visualize IAM role inheritance across your GCP environment and highlight users or service accounts with inherited high-privilege access – all available within one prompt.
Sola apps that could help you
Visit the App GalleryHow to track inherited permissions in Google Cloud Platform
1. Understand how permission inheritance works
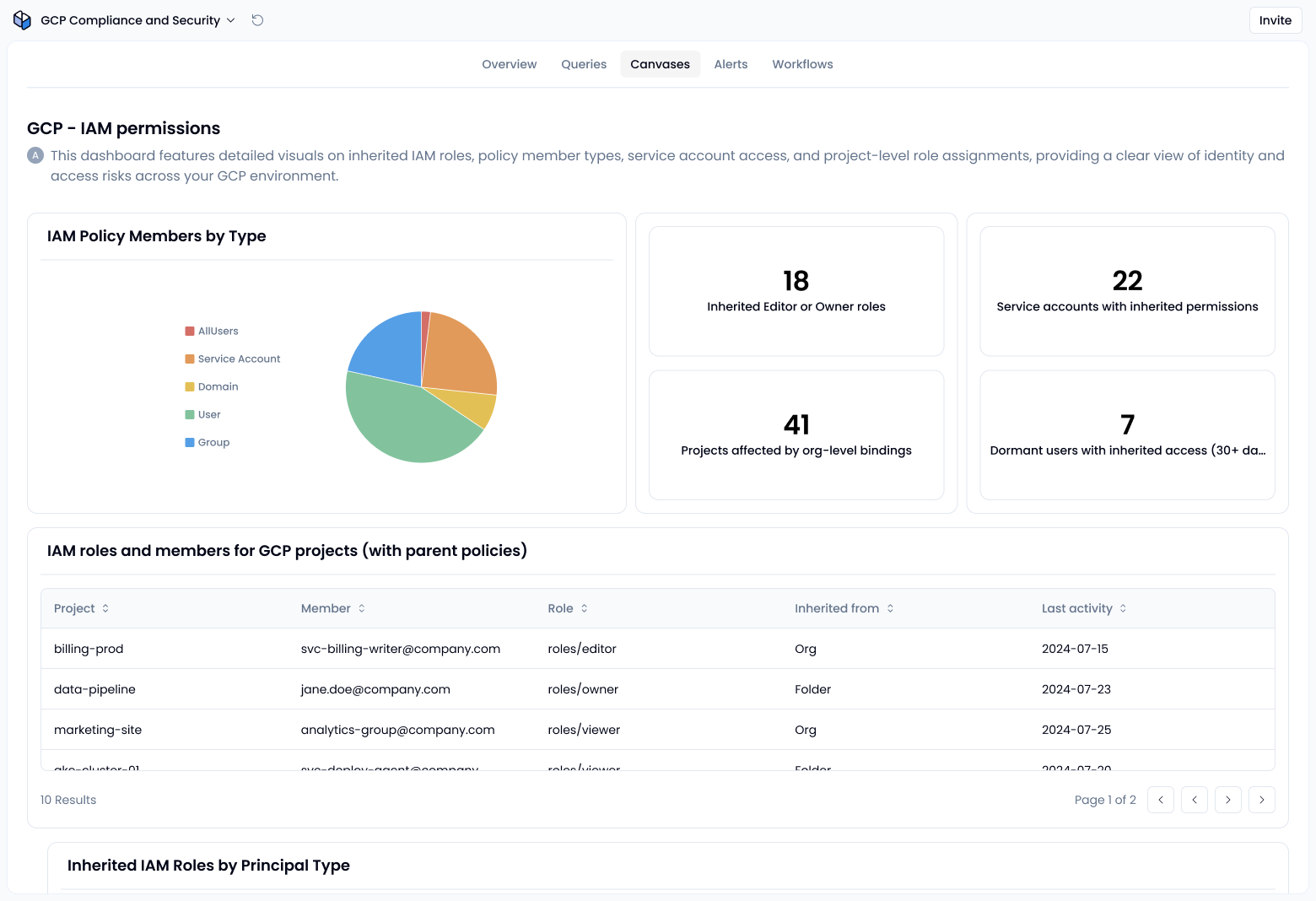
In GCP, IAM roles assigned at a higher level such as an organization or folder automatically apply to all nested projects and resources unless explicitly overridden. For example, a viewer role at the org level gives access to everything underneath it.
To audit effectively, you need a clear view of who got what access, where it came from, and whether it still makes sense. Sola’s AI helps you break this down without writing queries or manually pulling policies.
2. Identify inherited roles and where they apply
List all IAM bindings and focus on:
- Roles assigned at the org or folder level
- Accounts that don’t have direct project bindings but still have access
- High-privilege roles like Editor, Owner, or custom roles with wildcard permissions
An AI assistant would help you to instantly identify inherited permissions and group users based on access level, source, and usage.
3. Review risky inheritance patterns
Common problems include:
- Service accounts inheriting roles across unrelated projects
- Dormant users with inherited permissions from outdated org-level groups
- Broad roles like roles/*Admin assigned too high in the hierarchy
Use filters to detect accounts with inherited Editor, Owner, or custom roles. Then assess whether this access can be scoped more narrowly.
4. Automate periodic audits with AI
Manual IAM audits rarely happen consistently. Using a platform like Sola, you can create recurring reports or alerts using AI-driven logic. For example, you can automatically surface when new users receive inherited permissions or when high-privilege access appears in unexpected places. It’s a smarter way to maintain continuous visibility across your GCP identity surface.
Monitor and avoid hidden access with Sola
Sola helps you create your own GCP access audit app to monitor, flag, and visualize permission inheritance issues across your cloud environment. Get started with writing a prompt like “See all users, groups, and service accounts with permissions inherited from parent resources“, connect your Google Cloud environment – and you’re good to go.
Answer more security questions
How to monitor GCP audit logs for compliance?
How to enforce least privilege on all platforms
How to monitor security risks across cloud accounts?