Filter GitHub Dependabot alerts by dismissal status
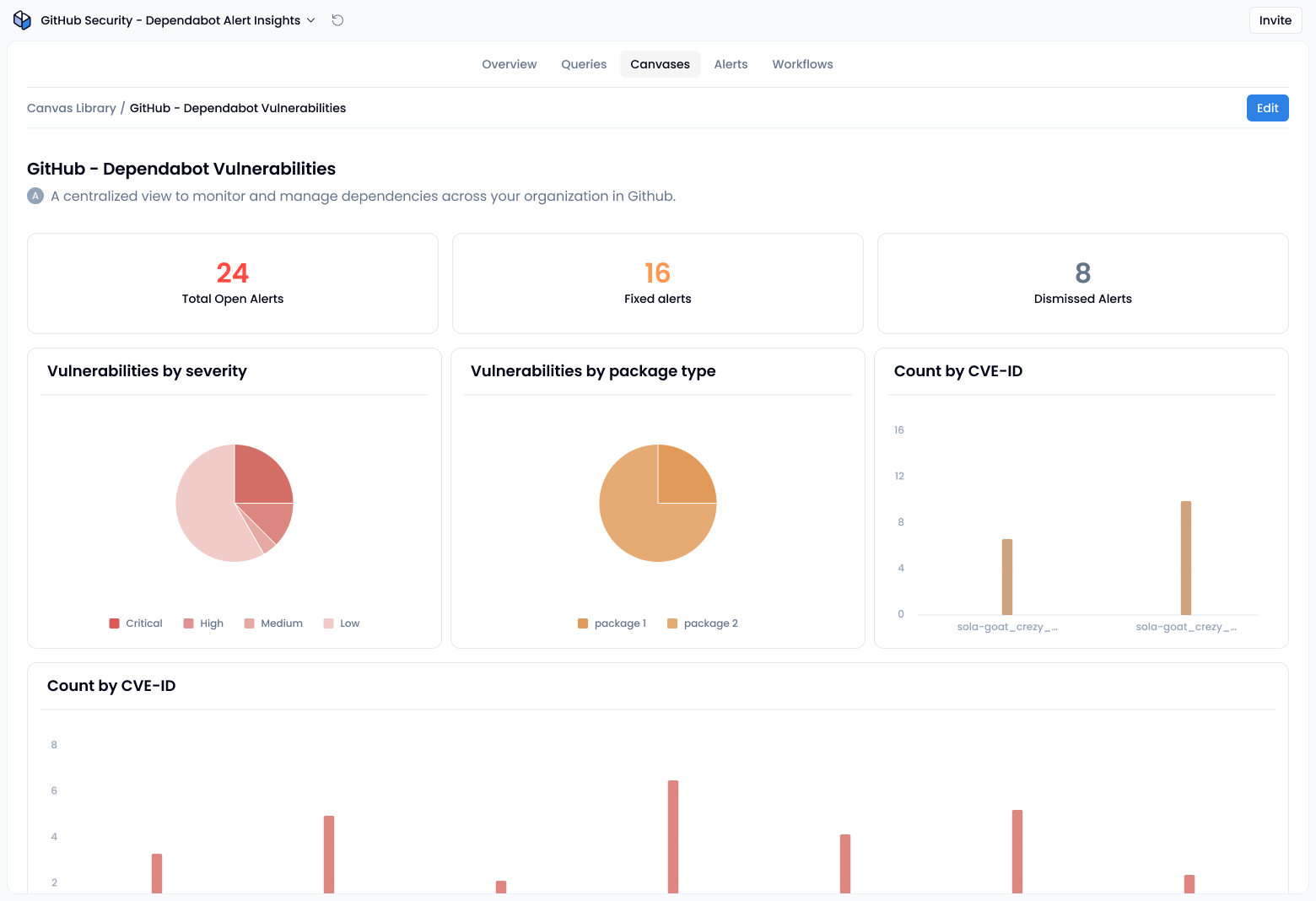
With Sola, you can use our AI assistant to track dismissed Dependabot alerts across your entire GitHub org. Surface dismissal reasons, audit trails, and trends in one place. No scripts or manual digging needed. The main advantage of using Sola here is the ability to cross-reference this data with additional sources and integrations, which you simply wouldn’t have if you were relying on GitHub alone.
Sola apps that could help you
Visit the App GalleryHow to review dismissed Dependabot alerts across repositories
1. Use GitHub’s built-in filters
Start by checking alerts in the Security > Dependabot section of each repo. From there:
- Switch to the Closed tab
- Filter alerts by Dismissed status
- View who dismissed each alert, and the stated reason like “won’t fix” or “false positive”
This gives a basic audit trail but lacks organizational coverage. There’s no default GitHub view for comparing dismissal activity across multiple projects.
2. Centralize visibility across your GitHub org
To audit dismissed alerts at scale, you can query GitHub’s GraphQL API or use a dedicated security tool. With Sola’s Dependabot alerts insights app, you get:
- A single dashboard showing all dismissed Dependabot alerts
- Breakdown by repository, user, severity, and dismissal reason
- Patterns across time so you can catch spikes or repeated behavior
The AI assistant helps you instantly identify anomalies, like when a developer dismisses multiple high-severity vulnerabilities without peer review.
3. Track patterns and prevent risky dismissals
Dismissals are not always a problem. But if left unchecked, they can hide legitimate threats. Use trend data to:
- Spot sudden increases in dismissals before key release cycles
- Flag repositories or users with unusually high dismissal counts
- Investigate repetitive use of vague justifications like “won’t fix” on critical alert
This helps maintain accountability and improves your overall GitHub security posture.
Monitor Dependabot alerts with Sola
Sola makes it easy to monitor Dependabot security alerts across your GitHub organization. Use our AI assistant to surface dismissed alerts, analyze security trends, and highlight blind spots across your repos. No code required.
Answer more security questions
How to monitor GitHub production deployments?
How to track GitHub deployments without CI/CD pipelines?
How to check GitHub repo branch protection?