Connect your cloud accounts, track misconfigs, get alerted.
The smarter way: plug your cloud accounts into a system that instantly flags misconfigurations, exposed services, and weak access controls. No need to manually query IAM roles or grep your audit logs. Just set it up once, define what you care about (like unrestricted access or public buckets), and get alerts when things go sideways across cloud platforms.
And that’s what Sola get you: use our AI co-pilot to create the app you need to monitor your cloud environments, connect your data – and you have your app, without an army of consultants and a three-month rollout plan.
Sola apps that could help you
Visit the App GalleryWhat does good cloud security monitoring actually look like?
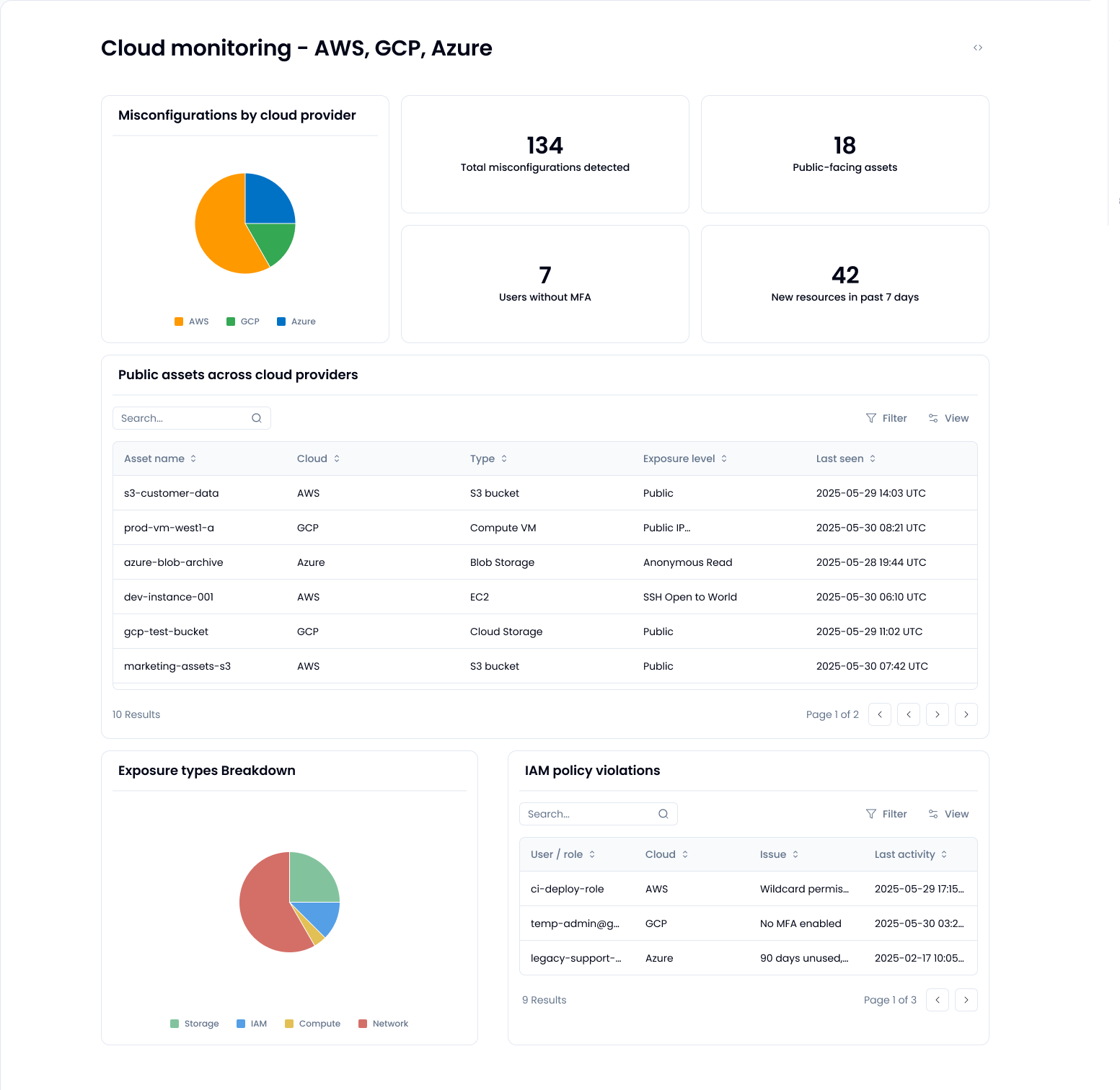
It’s not just a dashboard or another log aggregation UI. It’s a continuous check of the actual risks that matter, across every cloud account. Here are the basic four legs you should look for in your cloud security posture solution:
- IAM issues: Users without MFA, roles with wildcards, or service accounts that haven’t been touched in months, but still have access to prod.
- Storage exposures: That “temporary” public S3 bucket which could still be public, and now it has sensitive data.
- Network risks: Security groups with 0.0.0.0/0 inbound rules, or forgotten firewalls that allow SSH from anywhere.
- Drift over time: A new service account gets created. Someone spins up a public IP. You didn’t authorize it, but now you know.
Now, multiply that across all cloud accounts, and get them in one place. Sounds like a three-week project to build it, but with Sola, it would take you minutes.
Best practices: Monitor what actually matters
- Start with misconfigurations, not vulnerabilities: CSPM tools love to drown you in CVEs. But most breaches don’t start with an exploit, they start with bad config. Focus on wide-open ports, over-permissive IAM, and exposed storage. These are quite easy to fix and high risk.
- Go multi-cloud, or go blind: Many teams end up with workloads spread across AWS, GCP, and Azure, not always because of some grand multi-cloud strategy, but because someone needed a service fast and defaulted to whatever was easiest or already set up. But now you’ve got real assets in multiple clouds, and unless you’re monitoring all of them together, you’re missing part of the picture, and a unified view across all your cloud providers becomes essential.
- It’s not just about what’s exposed now: It’s about what’s changing. Who created that new user? Why are there suddenly five more public IPs? A good posture management solution should continuously tracks these changes and give you just enough signal to know when something’s off, before it hits production.
Implementation: With vs. without a real solution
Let’s talk about what happens when you don’t have a proper tool for cloud security monitoring.
You’re stitching together half a dozen consoles. Maybe pulling IAM data from AWS Config, poking around GCP’s Security Command Center, and trying to parse whatever Azure thinks a risk looks like. You’re juggling Terraform state files, spreadsheets, and probably a few shell scripts. And when your CTO asks, “Are we exposed anywhere?” – you still don’t have a confident answer.
If you go the “big vendor” route, it’s a different headache. You’ll get a polished UI, after 30 days of sales calls, onboarding, and a commitment that costs more than your annual cloud bill. Oh, and good luck customizing anything. Want to tune out the noise or track a metric unique to your setup? File a support ticket and wait.
Sola skips all of that.
You create your workspace. You connect your cloud accounts. You define the questions you care about, like, “Show me all public-facing VMs” or “Flag new service accounts with admin rights.” You ask Sola AI, and within minutes, you’re not in the dark anymore; You’re not overpaying for bloated dashboards. You’re running your own, focused security monitoring system – built for your real environment.