Inventory identities, check roles, enforce compliance
Azure managed identity simplifies secure access to Azure resources without handling credentials directly, but tracking identity assignments can get messy fast. Assignments tend to accumulate quietly, often with broader permissions than necessary, creating significant risks for Azure security and compliance if left unchecked.
Instead of manually sifting through resource groups and access controls, you can quickly build your own app using Sola’s AI. This lets you instantly see exactly where identities are assigned, their scope, privileges, and activity, all tailored specifically to your Azure environment.
Sola apps that could help you
Visit the App GalleryBest practice: Comprehensive inventory and scope Analysis
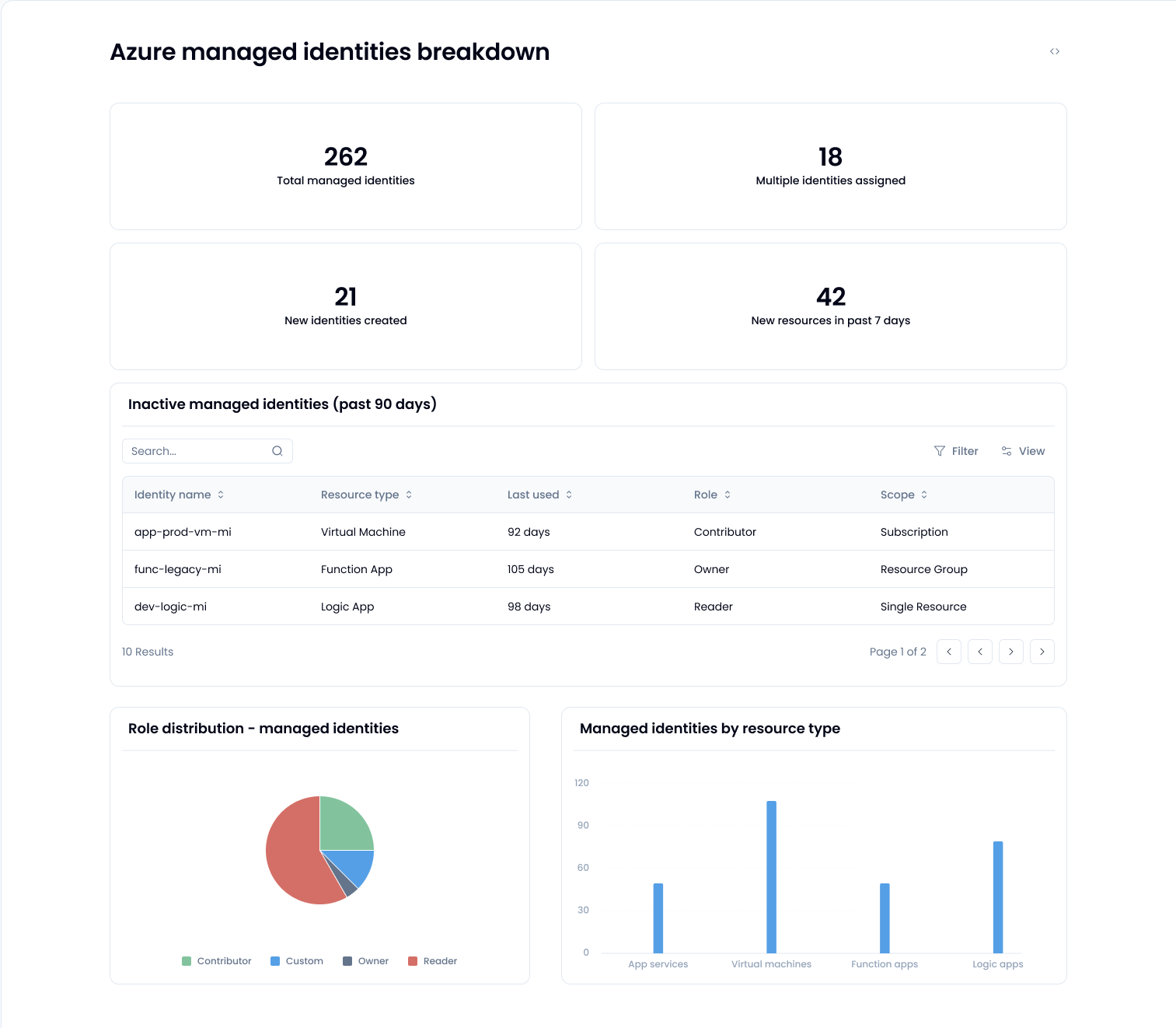
The first step in managing Azure managed identity assignments effectively is building a comprehensive inventory. You need complete visibility into every Azure resource – whether it’s virtual machines, app services, logic apps, or functions – that uses a managed identity. Tools like Azure CLI (az identity list) and Azure Resource Graph can assist here.
Once you’ve mapped out all assignments, perform a thorough privilege and scope analysis. Highlight identities with elevated privileges, especially those assigned roles like Owner or Contributor at subscription or resource-group levels. These broad permissions are typically unnecessary and a common compliance issue.
Strategy: Detect over-privileged and inactive identities
Regularly detecting over-privileged and unused identities is critical. Identities granted excessive privileges can become attack vectors, especially when left unused and forgotten for extended periods. Identify any identity not used in the last 90 days and those assigned permissions beyond their functional need.
With automated detection, you can flag and remediate these identities quickly, significantly reducing security exposure and ensuring ongoing compliance with Azure security best practices.
Tips: Enforce least-privilege and track changes
Maintaining least-privilege access, assigning identities only the permissions required, is fundamental. Always prefer Reader or tailored custom roles over broader ones like Contributor. Monitor monthly changes and role assignments to detect privilege creep early.
Because let’s be honest: “temporary” Contributor access never stays temporary. If you’re not watching for scope creep, you’re basically inviting it in for coffee.
Staying vigilant prevents unauthorized access and aligns your practices closely with established Azure compliance standards.
Take control of Azure managed identities with Sola
Forget rigid dashboards or generic “cloud posture” tools that make you dig for answers. With Sola, you just describe what you want to know, like “which managed identities haven’t been used in 90 days and still have Contributor access” – and our AI builds the app for you in minutes.
You get exactly the logic you need, shaped by your own prompt, with full visibility into all managed identities: their assignments, roles, scopes, activity, and compliance status. Whether you want to flag privilege creep, enforce least-privilege, or just make sure nothing weird has changed this month, Sola turns your question into a working security tool.
Answer more security questions
How to monitor security risks across cloud accounts?
How to audit file sharing across Google Workspace?
How to find Okta users without MFA?