
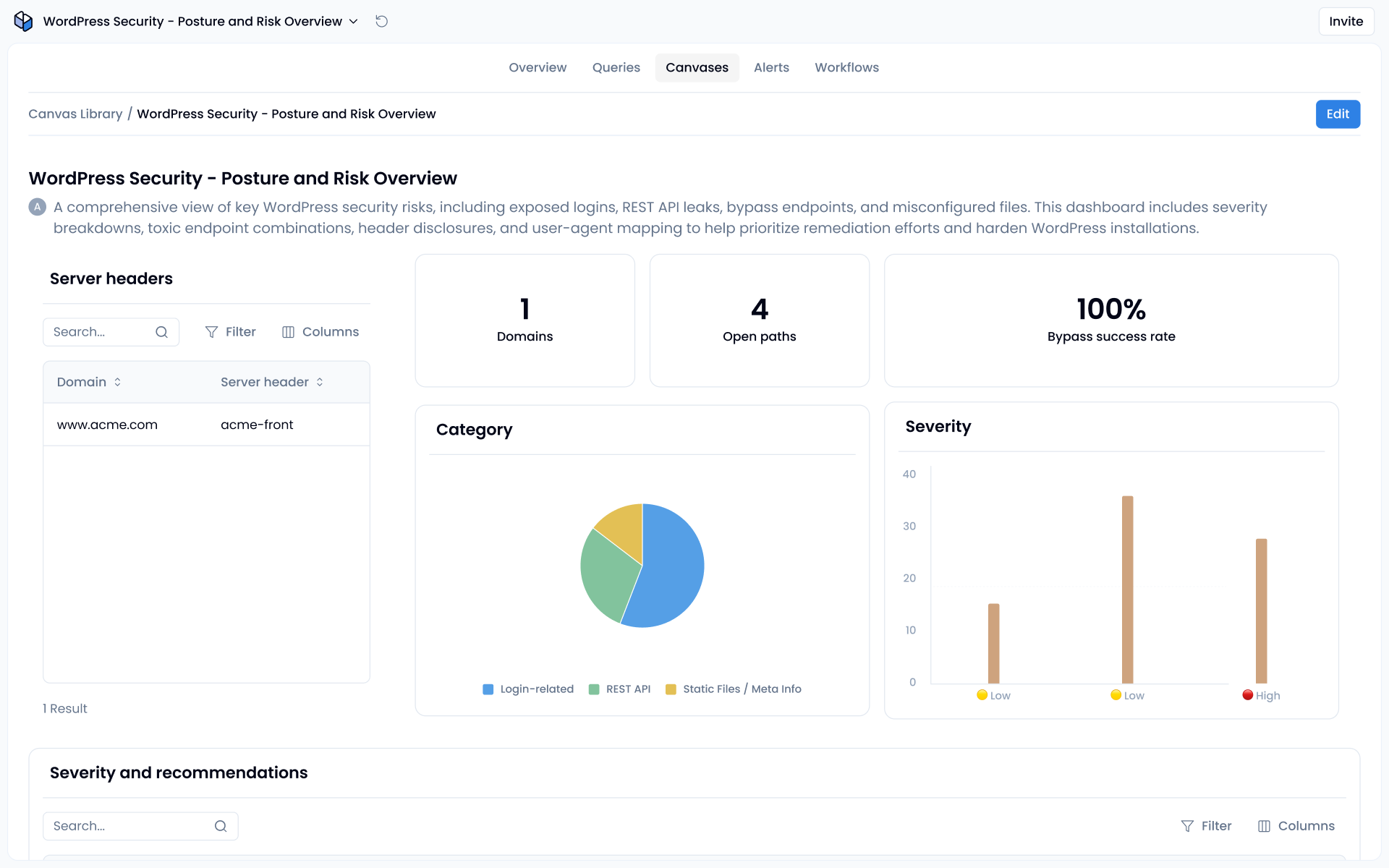
Picture the scene: marketing needs a micro-site for a new campaign, so a junior dev (or worse, an outsource junior dev) creates a WordPress landing page on an idle VM, grabs a theme, and e-mails the URL. No change-control, no WordPress security scan, and certainly no CISO sign-off.
Two weeks later your SIEM lights up with traffic from botnets poking encoded URLs and guessing logins. A small oversight in website security snowballs into a full-blown breach.
That whirlwind setup is common in WordPress land. Its plug-and-play ease often skips the hardening steps, leaving silent gaps that attackers love to exploit.
Below are four under-discussed WordPress vulnerabilities. For each, you’ll see how the hole appears, why it matters, and what to do about it, with only one brief nod to AI where it genuinely helps.
Sensitive path bypasses
Why it happens and the risk
Your WAF blocks a clean request to /wp-login.php with a 403. That looks safe until an attacker tries /%2Fwp-login.php, %252fwp-login.php, or //wp-login.php. On many Nginx-backed WordPress setups the path is decoded or collapsed after the security check, so the WAF inspects gibberish while the origin sees the real login page and serves it. One encoding trick can turn a blocked resource into an open door for credential-stuffing bots.
How to fix it (with AI)
- Decode first, decide second. Configure the WAF to normalise URLs before its rules run.
- Restrict by source. Allow the login path only from trusted IPs such as office ranges, VPN gateways, or a jump-box.
- Add MFA at the application layer. If someone still reaches the page, a second factor stops recycled credentials.
- Verify continuously with an AI assistant like Sola. Prompt it with “Show me unprotected login interfaces for example.com.” The assistant probes encoded variants, returns a table of vulnerable paths, response codes, and suggested filter rules. Tighten the rule it flags, rerun the prompt, and iterate until the list comes back empty.
These measures, backed by continuous AI verification, shut down the majority of WordPress bypass attempts and keep the gate to your login panel firmly closed.
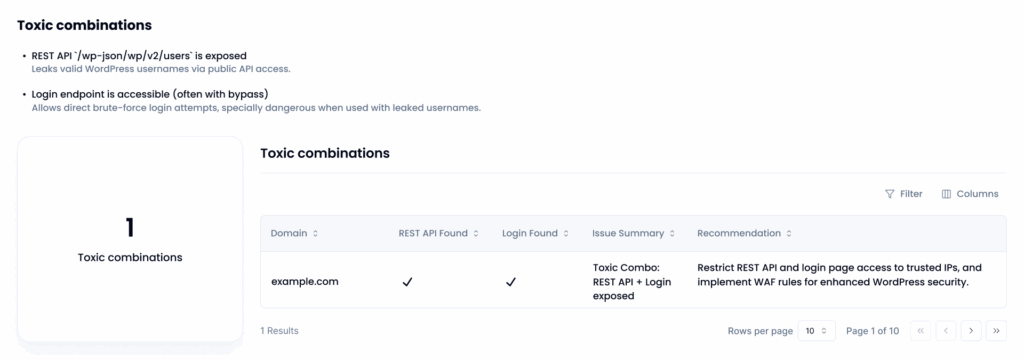
The toxic combo: exposed login plus public REST API
Why it happens and the risk
wp-login.php is the front door for brute-force tools, while /wp-json/wp/v2/users (and related endpoints) can leak valid usernames. When both stay open you create a toxic combination: attackers harvest usernames through the REST API, then feed them straight into automated password-guessing on the login page. Success rates rise sharply because guesses are now against real accounts, not random names.
How to fix it
- Lock down the login page. Enable rate-limiting or CAPTCHA, enforce MFA, and rotate any stale passwords.
- Restrict the REST API. Require authentication for sensitive routes, allow the API only from trusted IP ranges, or disable the
usersendpoint completely to prevent username harvesting. - Check for bypasses. An attacker who finds
/wp-login.phpthrough an encoded URL can also hit/wp-json/wp/v2/usersthe same way. Make sure the WAF rules that block login bypasses also protect the REST path.
Sola’s WordPress security risks scanner tests both endpoints in the same scan, flags any site where they are simultaneously reachable, and surfaces the evidence in one view that lists the exact URLs, response codes, and source IPs involved.
Information leaks via headers and forgotten files
Why it happens and the risk
Headers like Server: nginx/1.22.1 and stray files such as readme.html expose exact versions and internal paths, giving attackers a shortcut to the right exploit.
How to fix it (with AI)
Strip version headers at the web server or proxy, disable directory indexing, and run scheduled sweeps for files like .zip, .~, or wp-config.*. A conversational AI assistant makes the sweep painless by simply asking:
“Scan example.com for HTTP response headers that disclose server or PHP versions and list any public files in web root that contain credentials or version info.”
You’ll get a concise table showing every leaking path, the header value or file name, severity ratings, and recommended configuration lines such as Header unset Server.
Issues’ classification by severity
Why it happens and the risk
Many scanners dump cosmetic alerts alongside critical flaws, flooding teams until high-impact WordPress security issues languish untouched.
How to fix it (with AI)
Adopt a severity rubric that weighs exploitability and business impact, then enforce SLAs such as fixing High issues within 24 hours.
A quick prompt to your AI assistant keeps the backlog sane. You can write a question like “Show only High and Medium findings for example.com, grouped by endpoint with remediation steps.”
The assistant filters noise, tags exposed admin pages as High and info leaks as Medium, and hands you a concise, ranked list instead of a CSV avalanche.
Get started with Sola’s AI assistant
WordPress vulnerabilities – key takeaways
That marketing micro-site you approved at the last minute is part of your attack surface, whether you like it or not. Treat it the same way you treat any customer-facing service.
- Acknowledge the risk
WordPress websites are fast to deploy and just as fast to expose bypass paths, leaked headers, and over-permissive uploads. If it runs in production, it belongs in the security program. - Run structured checks
Schedule a WordPress-specific scan that tests encoded URLs, hunts for toxic combinations, verifies header hygiene, and flags dangerous HTTP verbs. Repeat after every content or plugin change, not just major releases. - Use AI to stay current
AI solutions for cybersecurity like Sola can filter findings by severity, surface only new leaks, and point you to the exact rule or header to update. One short prompt replaces manual log dives and reduces alert fatigue.
Bake these steps into your regular playbook, and the next time marketing sets up a site, security will already have it covered.
Senior Security Engineer, Sola Security
An innovative cybersecurity powerhouse, excelling in penetration testing, security architecture, and cloud wizardry to expose risks others overlook.
