
Graphs have always sat at the heart of security, and that role has only intensified as cloud stacks balloon in size. Previously, at Cider Security, I walked through mapping repos, pipelines, secrets, runners, and cloud creds into a single cybersecurity graph that mirrors an attacker’s thought process.
Today we’ll revisit that concept in the age of large language models (LLMs) and show why the union of graph structure with AI in cybersecurity is the fastest path from hype to something teams can actually ship. Short version: a graph gives LLMs the pinpoint accuracy and transparency that flat data never will.
Why cybersecurity is falling behind in the vibe‑driven era
LLMs have already rewritten the software playbook, yet uptake inside SOCs is lagging. In app development, you can tolerate high‑temperature outputs: slight artistic drift is a price teams would pay for rapid iteration. Security isn’t as forgiving: defenders need recall, precision, and receipts.
Agentic cybersecurity systems promise to merge findings, layer context that once took days to gather, and slash triage time. The legacy spray‑of‑alerts model only piles on fatigue, even when runtime analysis sweetens the pot. Flat findings are still noisy because too many hard‑and‑soft variables collide. That noise is also the breeding ground for vibe coding security vulnerabilities – bugs slipped in when speed trumps scrutiny.
Ground the model in policy, risk posture, and live environment data, and the workflow flips. Imagine agents that start from organizational signals – policy, risk appetite, asset criticality – and marry them with real‑time configs and threats. Instead of wading through thousands of static issues, analysts could chat about what matters this morning, next sprint, or next quarter.
Grounding and explainability: where LLMs stumble in security
Token prediction is the Achilles’ heel of AI in cybersecurity. Ask a model to write a poem and countless next tokens are fine. Assessing an EC2 instance is different: one wrong token such as mis-tagging a security group or skipping an ingress rule kills the verdict.
Low level decisions must be caged by evidence. You can’t hand wave a security group when measuring lateral movement risk. High level orchestration can handle broader guesses because analysts iterate the hypothesis.
Explainability is the covenant with auditors and engineers. Without a cybersecurity graph, you’re asking them to trust a probabilistic word salad. They’ll ask, “Why did I get this alert?” and you’ll have nothing but a token stream. A graph solves that: each claim boils down to a visible path – nodes, edges, and assumptions – an explicit audit trail.
Enter the graph: structure that tames the noise
Graphs smash sprawling documents into tidy, typed relationships. Model the world as nodes and edges like EC2 → HAS_SG → SG → ALLOWS → CIDR and the agent stops guessing across hundreds of tokens; it navigates a bounded space anyone can inspect.
Graph form:
![(i-0a12) -[HAS_SG]- (sg-0aa1) -[ALLOWS {proto:tcp, port:22}]- (0.0.0.0/0) (i-0a12) -[HAS_SG]- (sg-0bb2) -[ALLOWS {proto:tcp, port:5432}]- (10.0.2.0/24) (i-0a12) -[HAS_SG]- (sg-0aa1) -[ALLOWS {proto:tcp, port:22}]- (0.0.0.0/0)
(i-0a12) -[HAS_SG]- (sg-0bb2) -[ALLOWS {proto:tcp, port:5432}]- (10.0.2.0/24)](https://sola.security/wp-content/uploads/2025/08/736x440-1.png)
(i-0a12) -[HAS_SG]- (sg-0bb2) -[ALLOWS {proto:tcp, port:5432}]- (10.0.2.0/24)
Raw JSON:
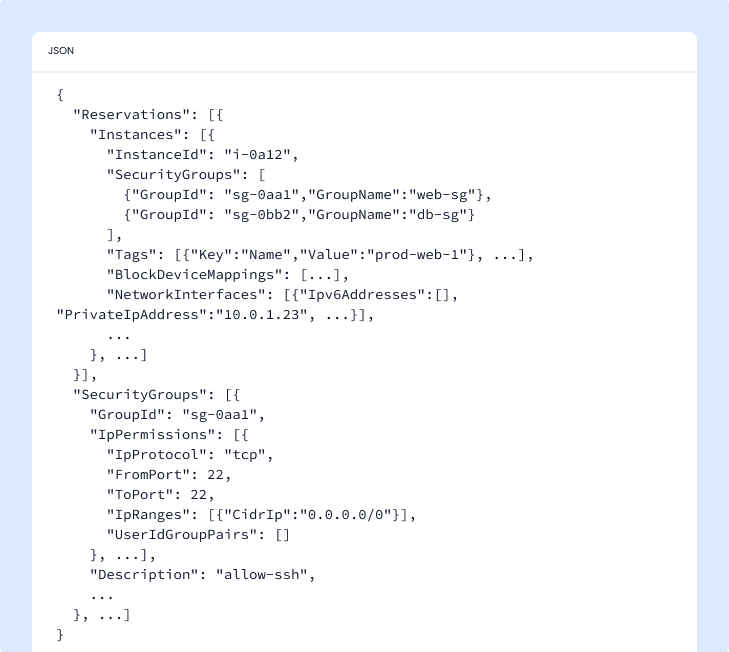
To reach the same verdict from JSON, the model must:
- Find
i-0a12deep in nested arrays - Pull its security group IDs
- Cross reference a separate
SecurityGroupsblock - Parse each
IpPermissionsarray - Decode
IpRangesto grasp network reach
That’s a brittle, multi hop chain where every step invites hallucination.
The security graph, on the other hand, delivers a near deterministic hop: (i-0a12) → (sg-0aa1) → (0.0.0.0/0). Attention narrows to semantically rich edges, cutting both context entropy (input ambiguity) and generation entropy (how many next tokens make sense). Low entropy means higher precision and effortless explanations like “We flagged lateral movement because edge X→Y exists while rule Z allows it.”
If you are using Sola, this is where the new Graph Research mode steps in. Flip it on and the copilot automatically draws these paths, highlights toxic combinations, and shows the blast radius for any critical issue – all inside a clean visual canvas that proves exactly why a finding matters.
Microsoft’s GraphRAG backs the entropy claim. Graph based retrieval beat plain vector RAG in 72 to 83 percent of head to head matchups, while summaries at the graph’s root needed 97 percent fewer tokens and still trumped text only RAG on global reasoning.
Beyond entropy cuts, GraphRAG answers queries text RAG cannot. “Which Lambda functions touch secrets?” Evidence like roles, policies, and ARNs is scattered across services. A graph walks every Lambda to Secret path and surfaces the real exposures. Graph Research does the same trick across cloud, SaaS, and code in one click.
Scale and meaning: the twin obstacles
Even the neatest cybersecurity graph keeps growing. Graph databases remain touchier than relational stores, scale worse, and demand disciplined modeling or they bog down and cost a fortune. Tack on the shortage of graph expertise and adoption hits a wall.
The scale hurdle
Cross vendor ecosystems are monster graphs. Fitting the lot into a context window is laughable. Token costs explode and caching gains vanish.
Potential fix: treat sub graphs as first class RAG chunks, serving a focused slice tailored to the specific inference run. Graph Research already does this behind the scenes, pulling only the slice of the Sola security graph that answers the question.
Mind the semantic gap
Single edges are crystal clear (A → B), but paths aren’t. Does A → B → C imply A can reach C? Many agents overstep or misread the chain.
Potential fix: pair graph vectors like A → B → C with embedding vectors to bolt on missing semantics.
Cybersecurity graphs: the practical way forward
None of the hurdles mentioned in this article are deal breakers. They’re design puzzles. Hybrid patterns already surface: RAG to deliver task specific sub graphs, embeddings to bridge semantics, and more. Nail those, and defenders can finally talk with AI about what matters now, next sprint, or next quarter without drowning in static alerts.
Sola’s way forward
Graph Research is now available as an optional reasoning mode in the Sola AI copilot. When enabled, it activates automatically for deeper multi system questions, pulls from Sola’s proprietary security graph, and returns dynamic visuals that spell out connections, risk origins, and impacted assets. Keep it on to get enterprise grade insights, or toggle it off for quick one liner checks. Either way, the graph is there when you need it, and that is how AI in cybersecurity moves from guessing to knowing.
CTO, Sola Security
Leon has spent over a decade scaling security products and leading engineering teams at Cider Security, Palo Alto Networks, Red Hat, and Snyk, and now serves as CTO at Sola. When he’s not architecting complex systems, he’s probably debugging something from the back seat of a taxi.
